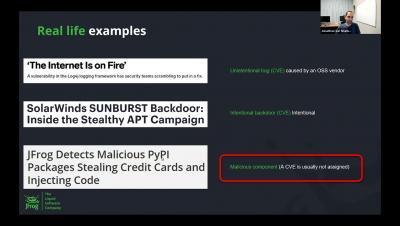
Threat-Based Methodology: An Introduction
This three-part blog series will explore threat-based methodology and how it benefits every company with a network. The series leverages the analysis presented by the Federal Risk and Authorization Management Program (FedRAMP) Program Management Office (PMO) in conjunction with the National Institute of Standards and Technology (NIST).