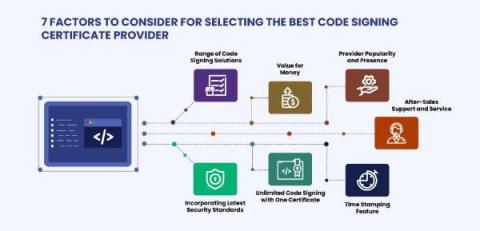
Unconstrained Delegation
Unconstrained delegation represents a serious cybersecurity risk. By taking steps to abuse the Active Directory delegation controls applied to user and computer objects in an AD environment, an attacker can move laterally and even gain control of the domain. This blog post explores this area of attack (unconstrained delegation) and offers security teams and administrators effective strategies for mitigating this security risk.