Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
GitGuardian Code Security Platform Now Available on AWS Marketplace
With GitGuardian available on AWS Marketplace, we’re making it easier for all organizations using AWS to protect their software supply chain from exposed secrets and credentials.
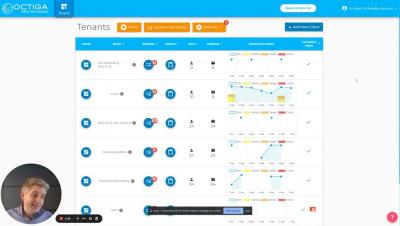
Delivering Continuous Office365 Security Audits
The Importance of Isolated Backups for Cybersecurity
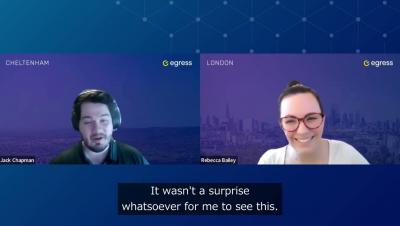
Email Security Risk Report discussion
Download your copy of the 2023 Email Security Risk Report here: https://egress.co/ufxrO
Find out more about our products at: https://www.egress.com/products
Cyber Counterintelligence (CCI): Offensive & Defensive Strategies for Cybersecurity
CIO vs. CISO vs. CPO: What's The Difference?
Manufacturing Predictions - the highlights for 2023
Why Australians Are Keen Adopters Of Managed Security Services
Australia is renowned for our willingness to adopt IT efficiencies! The ongoing shift to cloud computing both worldwide and here, seen recently in Amazon’s expansion to a second data center in Melbourne, shows that Australians are not afraid of outsourcing workloads to shared data center.
Kubernetes secrets management: 3 approaches and 9 best practices
Secrets, such as usernames, passwords, API tokens, and TLS certificates, contain confidential data that can be used to authenticate and authorize users, groups, or entities. As the name implies, secrets are not meant to be known or seen by others. So how do we keep them safe? The key to keeping secrets safe lies within how you manage them.