Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Nightfall AI Rightway Case Study Part 2
Nightfall AI Rightway Case Study Part 3 - Rightway Before & After Nightfall
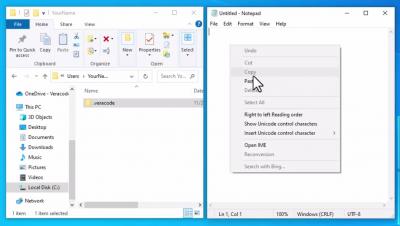
Install the Veracode IntelliJ Plugin
What is Malware as a Service (MaaS)?
Malware as a Service is the unlawful lease of software and hardware from the Dark Web to carry out cyber attacks. The threat actors who use this service are provided with botnet services and technical support by the MaaS owners. This service opens doors to anyone with minimal computer skills to use and distribute pre-made malware. The data that is stolen is often sold to the highest bidder or left for the service subscribers. MaaS is an illegal version of Software as a Service (SaaS).
Stop Working in Silos: Integrating with APIs
Is your security tool an island? Does it do its singular task with little more to offer than what it says on the package? Too many security offerings behave as singular entities, forcing you to constantly perform task switching to complete a job. If you are using a robust tool, then you may not be taking full advantage of its capabilities. Many capabilities of a good tool can be broadened with the use of an Application Programming Interface (API)
The Top Cyber Attacks of February 2023
Building smarter DevSecOps with Intelligent Orchestration
New in Vanta | February 2023
February’s product update includes many exciting announcements from Vanta. We announced Custom Frameworks and Controls and other improvements to the Vanta experience: