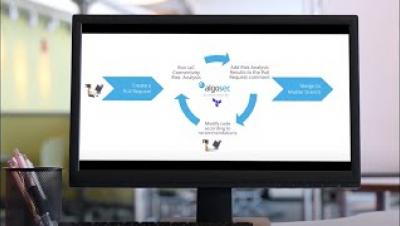
Get Smart(er) about the business value of API security
API attacks have dominated the cybersecurity news cycle lately. In early 2023, T-Mobile made news for an API-based breach of 37 million PII records of its past and present customers. And last year, Optus, a major telecommunications company in Australia, experienced an API security incident that exposed around 10 million customer records. And API attacks that aren't quite as ”newsworthy” happen every single day.