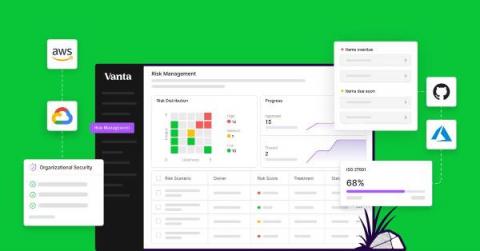
What is a trust management platform?
When you start pursuing compliance for a particular security standard, you do it with a specific goal in mind. Maybe you’re pursuing compliance because it’s a legal requirement in your industry or because a prospective customer requires it. But what happens after you achieve that initial SOC 2 or ISO 27001? It’s easy to get caught up in checking the boxes and lose sight of the why behind your security and compliance work.