Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Look to the Future of Borderless Data Protection
Fast application security testing with the Polaris platform
What is a quishing attack?
Phishing attacks have been the most persistent and widespread form of cybercrime for decades, but cybercriminals' tactics and methods are continually evolving. In the past, attacks were simpler and easier to spot. However, as technology has advanced, and more people go online, cybercriminals have become more sophisticated in their methods, making their attacks harder to detect.
Coffee Talk with SURGe: 2023-APR-25 The Interview Series live from RSA Conference
SecOps In Seconds: Creating Response Templates in Splunk Mission Control
Rubrik & Zscaler Announce Industry's First Double Extortion Ransomware Solution
While ransomware continues to be a growing problem, double extortion ransomware in particular has been growing even more rapidly for organizations. Zscaler’s ThreatLabz has found a nearly 120% growth in double extortion ransomware. Double extortion attacks are devastating for organizations because they involve both the encryption of production data as well as the exfiltration of data.
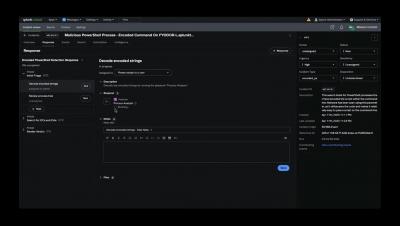
User Management via the Get-ADUser Cmdlet in PowerShell
The Get-ADUser cmdlet in PowerShell provides many parameters for finding one or more users in an Active Directory (AD) domain. By default, PowerShell runs using the account that is logged on to the machine. If you want to run a command using a different account, you can force PowerShell to prompt you for the credentials by using this switch before your command.
Cyber security and Critical Infrastructure: Are We Prepared for the Worst?
EP 26 - Ransomware Revisited: Combating the Identity Explosion
Andy Thompson, Offensive Security Research Evangelist at CyberArk Labs, returns to Trust Issues for a dive with host David Puner into the latest developments in the world of ransomware. With ransomware events on the rise, Thompson sheds light on the alarming trend of data exfiltration and double extortion. But what’s causing this surge? Thompson connects the dots between the rise of digital identities and the increasing frequency of ransomware attacks.