Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
A Closer Look at SecurityScorecard Marketplace
On average, organizations deploy 47 different cybersecurity solutions and technologies. This puts security, IT, and VRM teams in a difficult position, working with various tools that don’t integrate. One-third of organizations identify “non-integration of security tools” as a major roadblock to getting the total value of their investments.
New Study Reveals Shocking Truth About Data Breach Cover-Ups
The 5 Biggest Cybersecurity Risks for Businesses Using VoIP
RegTech for KYC & AML : What are the use cases to improve AML Compliance
The detrimental effects that financial crime may have on businesses and their consumers are nothing new to the fintech sector. When it comes to money laundering, this is especially accurate. Fintechs are attractive targets for money launderers since they only offer digital services, which they believe gives them more anonymity and makes it possible for them to perpetrate crimes undetected.
Candid Chats: How to transition to ISO 27001:2022?
The First Software Composition Analysis (SCA) Integration for ServiceNow With Snyk
RSA Conference 2023: Key Takeaways From Our Five Favorite Sessions
RSA 2023 is a wrap, but that doesn’t mean we are finished with the annual event. Sharing information, success stories, and lessons learned lies at the heart of RSA. And after a week of talking to attendees and pundits, giving demos, and gleaning knowledge from a slew of sessions, it’s going to take some time to sort through all the treasure from that trove of knowledge. For starters, here are a few of the more noteworthy sessions we saw at the show.
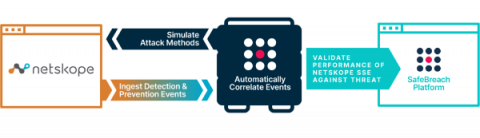
Validating and Optimizing your Security Service Edge Posture with SafeBreach and Netskope
Enterprise security operations teams find it increasingly difficult to maintain a hardened posture against advanced network and cloud threats. Given the rapid adoption of cloud platforms and software-as-a-service (SaaS) tools, cloud application traffic has overtaken web traffic to dramatically expand the attack surface. As a result, overreliance on traditional security controls can lead to increased blind spots, and control misconfigurations can create significant business risks.
Automate Reporting for Security Awareness Training Events and Suspicious Email Remediation Management with Cortex XSOAR and KnowBe4
Security teams face unique challenges in today’s rapidly-changing landscape of phishing, malware, and other social engineering and cybersecurity threats. Collaboration across disparate teams and siloed tools adds additional layers of complexity to security teams’ day-to-day operations. When security teams use different systems for simulated phishing, security awareness training, incident response and remediation, it is difficult to track and optimize the full lifecycle of an incident.