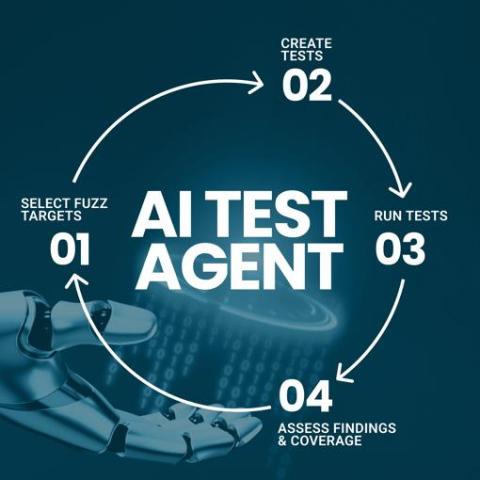
Simplify SOC Reporting with Customizable Dashboards
SOC teams often wrestle with clunky, siloed reporting tools that lack real-time, connected capabilities. Analysts end up buried under a mountain of fragmented xdata, forcing teams to spend valuable hours tracking down answers to their most pressing questions, rather than tackling threats head-on. At Torq, we feel SOC reporting should be your power move, not a painful process.