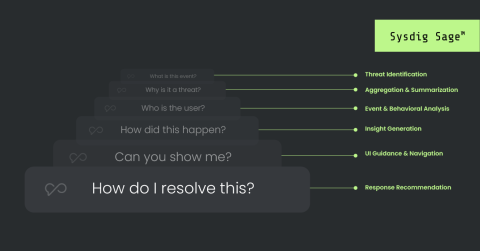
CISOs in Crypto
There are new generation of attack threats that AI has made much more dangerous (e.g. phishing, deep-fake schemes, and other AI-based attacks). There are also new crypto-related threats to be aware of, including attacks based on smart contract vulnerabilities, threats against exchanges, logic flaws, and more.