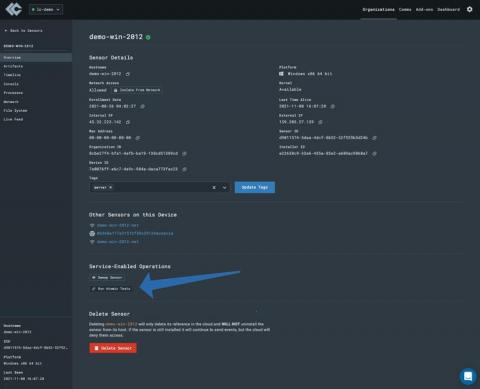
LimaCharlie & Atomic Red Team Enable a DevOps Approach to Cybersecurity
Engineering is both an art and a science. It requires creative thinking but is bounded by a rigidity which enables measurement and progress. We can only see so far because we stand on the shoulders of giants… and because those giants kept really good notes. Cybersecurity is growing up and it has to. Cyber is no longer the domain of shadowy figures in hoodie sweatshirts, it now has a presence in the C-suite.