Why Does LimaCharlie Exist?
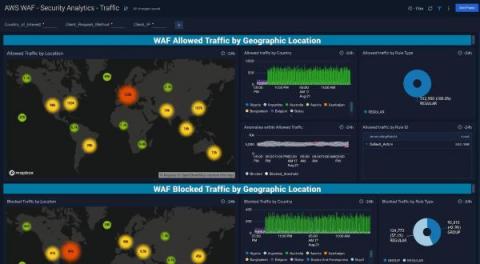
Security is an active market with new vendors emerging regularly. Here is a ”simple” example of what has become a common way to group companies in a logical way - a so-called cybersecurity technology map: This is a lot to take in, yet the above chart is one of the simplest illustrations available when searching “cybersecurity technology map”. A reasonable question could be - how did we get here?