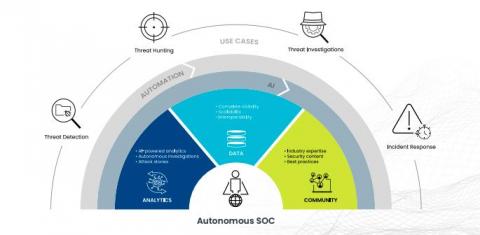
Emerging Technologies and Evolving Analysts Are Giving Rise to the Autonomous SOC
Fueled by the need to detect new, emerging threats while supplying meaningful feedback upstream to anticipate and prevent future ones, the modern SOC is the engine that protects organizations worldwide. The heart of that engine is common to all SOCs since they debuted more than a decade ago: people.