Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Integrate Arista CloudVision with Forward Enterprise to Automate Network and Security Verification
Network automation has many benefits for organizations adopting a DevOps model for managing their infrastructure, including speed, agility, and a consistent change control process. However, with improvements in speed, there comes an added risk of configuration errors rapidly propagating through the network. To safeguard against potential mistakes, network and security verification become an essential part of the network DevOps lifecycle.
How do Observability and Security Work Together?
There’s no question that the last 18 months have seen a pronounced increase in the sophistication of cyber threats. The technology industry is seeing a macro effect of global events propelling ransomware and wiperware development further into the future, rendering enterprise security systems useless. Here at Coralogix, we’re passionate about observability and security and what the former can do for the latter.
The Guide to Kubernetes Compliance
Kubernetes (K8s) has achieved undeniable mainstream status, with 96% of organizations currently evaluating or already using this technology, according to the Cloud Native Computing Foundation (CNCF). This popularity also brings growing scrutiny over Kubernetes compliance standards and audits, in light of how Kubernetes and cloud native technologies demand a very different approach to security.
4 Ways Your Passive Backups Can Drive Active Cyber Defense
Due to the proliferation of cloud-native environments, ransomware attacks have increased dramatically in recent years. Cybercriminals can access a variety of ransomware tools from anywhere in the world at a moment’s notice. This capability has produced an entire economy of Ransomware-as-a-service (RaaS). Despite significant investment in real-time infrastructure security tools, organizations are failing to quickly identify and recover from an attack.
Why CISOs Need to Care about Compliance Regulation in Cybersecurity
Compliance regulation is a necessary evil in the world of cybersecurity. As a CISO, you need to be aware of all compliance regulations that affect your organization so that you can ensure your security program meets these requirements while also protecting sensitive data.
Avoid the 3 Pitfalls of Native Database Auditing for Privileged User Monitoring
Regulations and frameworks such as PCI-DSS, SOX, NIST SP 800-53, NERC CIP and HIPAA require privileged user activity to be monitored and audited sufficiently for investigation. Privileged user monitoring and auditing for databases are critical as databases often contain the most sensitive information to an organization. Many organizations leverage built-in database auditing capabilities included with their databases to meet these monitoring and auditing requirements.
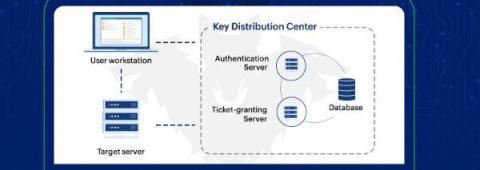
Kerberos and Active Directory
If you have been researching Active Directory (AD), chances are that you will come across the concept of Kerberos for user authentication and other service request-related functionalities. It is worthwhile to examine the Kerberos protocol in depth and, in turn, appreciate the dependency of AD on Kerberos. Given that Kerberos is an industry standard, you will see that it has become the most widely used network authentication protocol for all Windows environments with operating systems 2000 and later.
HIPAA Compliance: 5 Healthcare Cyber Security Vulnerabilities
The world of healthcare has gone digital. Records can now be transferred anywhere they are needed, from hospital to hospital, or even directly to the patient’s email inbox. While the digitalization of healthcare records is extremely convenient but it is now equally dangerous. These sensitive PHI data are exposed to various forms of cyber threats and vulnerabilities.
WatchGuard EPDR certified by OPSWAT as Gold Anti-malware
WatchGuard has obtained OPSWAT's GOLD distinctive insignia as a certified provider, demonstrating that its applications are powerful, reliable, and efficient. Products that receive the OPSWAT GOLD certification, such as WatchGuard EPDR, are highly compatible with the industry's leading NAC and SSL-VPN solutions, such as Citrix Access Gateway, Juniper Host Checker, F5 FirePass, etc. Gold-certified products can be detected by these solutions, and some remediation and evaluation actions are supported.