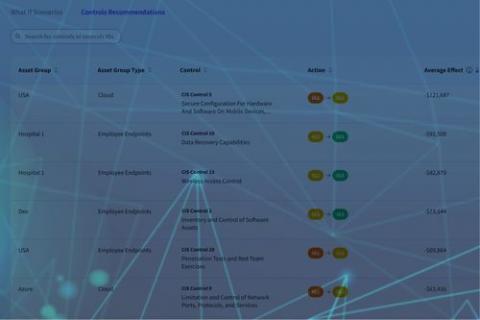
New Feature: AG Level Controls
Two years ago, Kovrr took a unique approach to cyber risk modeling of financial quantification (FQ) and expanded to the enterprise market. After a long time of quantifying risks of portfolios for global insurers and reinsurers, Kovrr was able to build expertise around quantifying risk with specific expertise in acquiring high-quality data to feed our models and fast time to value using automation.