The Ultimate Security Checklist to Launch a Mobile App in Nigeria - iOS & Android
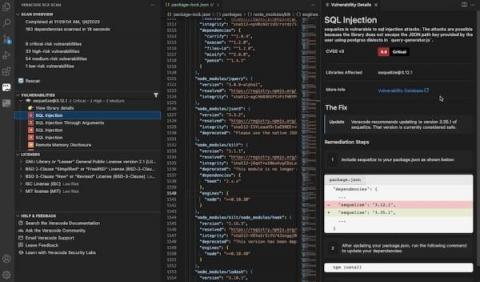
Nigerian authorities have made great strides in data security, and businesses worldwide are taking notice. If you're planning to launch a mobile app in Nigeria, it's crucial that you understand the importance of app security and take steps to ensure that your app meets Nigerian data privacy requirements. We’re aware that data protection can be overwhelming as it requires a holistic approach that incorporates legal, administrative, and technical safeguards.