Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
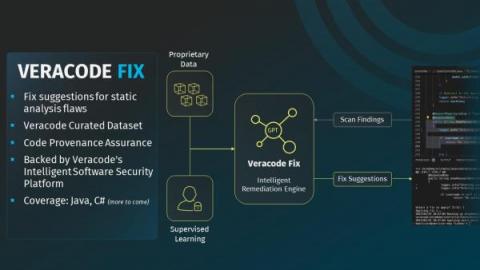
How to Measurably Reduce Software Security Risk with Veracode Fix
Veracode Fix is now available as an add-on to Veracode Static Analysis for customers on the North American instance. Availability for customers on Veracode’s EMEA and FedRAMP instances will be coming soon!
SecurityScorecard and the U.S. Chamber of Commerce
This week, SecurityScorecard is participating in the US Chamber of Commerce’s Cyber Security Trade Mission to Israel. This has been a valuable experience to not only share our cybersecurity knowledge, but to learn more about Israel’s cybersecurity efforts, and those of other countries.
Five Tips for Using SBOMs to Boost Supply Chain Security
A Software Bill of Materials (SBOM) is a key cyber defense item — it identifies what’s in your software, applications, and code base so that you can detect and mitigate risk more effectively. This is useful when it comes to application security because companies can only detect and fix vulnerabilities if they know what’s there in the first place. SBOMs give you that visibility. Consequently, SBOMs are now a “must-have” tool for most companies.
Threat Detection In 2023 Is Broken. Here's How to Fix It
Why have cyber incidents topped the Allianz Risk Barometer for the last two years in a row? Growing attack surfaces are partly responsible. Remote work, cloud migration, IoT use and other trends give cyber threats more places to enter and hide within networks. But there is another cause – deficiencies in the standard approach to threat detection and response.
Proxy Servers: An Overview and Comprehensive Guide
Tanium Unveils Total Experience for ServiceNow
Long Live The New King - Is Breached.co the New RaidForums Domain?
ARMO achieves SOC 2 certification: strengthening security and trust
5 Steps to Combating Emerging Threats with Network Security
In today’s rapidly evolving threat landscape, cybercriminals have become more sophisticated than ever, making it crucial to stay abreast of the latest trends and tactics. The challenge is exacerbated by the expanding attack surface as more devices and device types connect to enterprise networks: IT, OT, IoT and IoMT devices, all with known vulnerabilities that can be exploited.