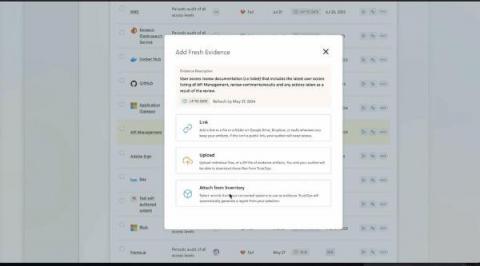
New In TrustOps: Evidence Automation with Smart Inventories
You want as much of your compliance program automated as possible, and collecting evidence to validate compliance controls always seems to take a lot of your team’s time. A considerable amount of control evidence involves providing accurate lists of artifacts to auditors — whether it’s workstations, tickets, alerts, or people. If only there were an easier way than having your teammates take screenshots and export lists from each of your internal systems.