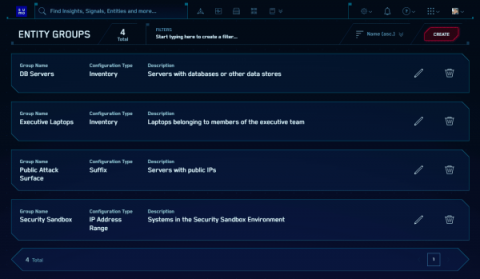
Meeting the 3rd-Party Risk Requirements of The NY SHIELD Act
The Stop Hacks and Improve Electronic Data Security (SHIELD) Act is designed to protect the personal data of all New York residents. This act broadens the data privacy and protection standards stipulated in the Gramm-Leach-Bliley Act (GLBA) and the New York Department of Financial Services (NYDFS). What makes this particular data protection law unique is its inclusion of biometric information, usernames, and passwords in the category of personal information.