Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Is it safe to write down your passwords?
Very few people can memorize all of their passwords – especially if they’re using unique ones for each account. Many solve this problem by embracing a password manager like 1Password, while others turn to pen and paper. The latter could be a tiny notebook, a whiteboard on their office wall, or an array of sticky notes attached to their PC monitor.
An unintimidating introduction to the dark arts of C/C++ vulnerabilities
As Synk announces its support of unmanaged dependencies (mostly C/C++ libraries), we thought it would be beneficial to introduce our non-C community to some common, high-risk dangers that lurk in the C world (get it?). Think of this as a “beginners guide” to C and C++ vulnerabilities, how they look, what problems they may cause, and how to fix them.
STRT-TA03 CPE - Destructive Software
The Splunk Threat Research Team is monitoring several malicious payloads targeting Customer Premise Equipment (CPE) devices. These are defined as devices that are at customer (Commercial, Residential) premises and that provide connectivity and services to the internet backbone. Examples include.
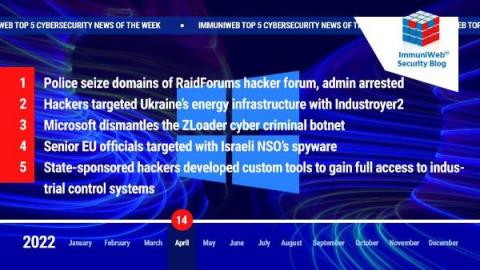
One of the World's Biggest Hacker Forums Dismantled in Global Law Enforcement Operation
Read also: Ukraine thwarts a Sandworm cyberattack against an energy provider, Microsoft disrupts the ZLoader botnet, and more.
How SecurityBridge & SECUDE offer additional layer of Data Security for SAP data
BlueHornet - One APT to Terrorize Them All
We Need a New Risk Management Approach to Secure Critical Infrastructure Against Russian Cyber Threats
A democratized approach to cybersecurity risk management that leverages continuous monitoring and public-private partnerships is overdue, and critical, for today’s cyber threat environment.
Customer Spotlight - Civo
For this customer spotlight we're highlighting Civo, a cloud-native service provider focused on Kubernetes. Bulletproof helps keep Civo's platform secure, giving peace of mind to their customers. In this edition we'll learn about Kubernetes and how it's rapidly becoming the de facto standard for managing cloud infrastructure to support modern applications. The COVID-19 pandemic has changed how we do business forever.
Cyber Security Tips for the Easter Holidays
The shortage of staff creates an urgency for organizations to have cyber security plans. For example, in 2021, the planned Kaseya ransomware attack happened on the 4th of July. Russian hackers knew there would be a staff shortage in the US. They used the company’s software to infiltrate the victims’ systems, using a zero-day vulnerability. As a result, the attack caused significant financial loss to 50 direct customers, and between 800 and 1,500 businesses down the chain.