Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Microsoft releases open-source tool for securing MikroTik routers
This blog was written by an independent guest blogger. In mid-March, Microsoft released a free, open-source tool that can be used to secure MikroTik routers. The tool, RouterOS Scanner, has its source code available on GitHub. It is designed to analyze routers for Indicators of Compromise (IoCs) associated with Trickbot. This article will introduce some background on the MikroTik vulnerability, the Trickbot malware, and some ways you can protect yourself.
CVE-2022-24675 - Stack overflow (exhaustion) in Go's PEM decoder
A few days ago it was reported that the new Go versions 1.18.1 and 1.17.9 contain fixes for a stack overflow vulnerability in the encoding/pem builtin package, in the Decode function. Given the high popularity of Go among our customers and in the industry at large, this update led us to investigate the vulnerability in previous versions.
How to convince your friends, family, and peers to start using a password manager
One of the many values of 1Password is that we make it faster and easier to use strong, unique passwords everywhere online. That’s great if you already have a good handle on why password strength matters for online security. But we know that not everyone does.
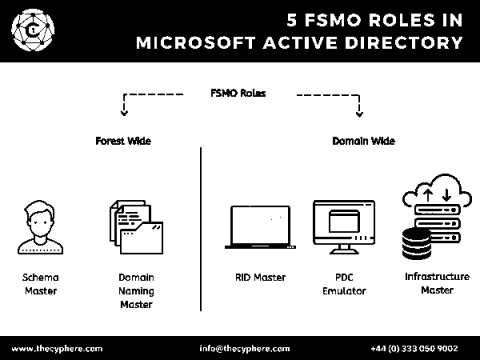
What are Active Directory FSMO roles and How do they Work
The FSMO (Flexible Single Master Operations) roles are vital when it comes to Active Directory. The FSMO roles help keep Active Directory consistent among all of the domain controllers in a forest by allowing only specific domain controllers to perform certain operations. Additionally, Active Directory FSMO Roles are essential for your Active Directory environment’s stability and security.
What is Incident Response?
Creating an incident response plan is mission-critical for modern organizations. As threat actors continuously evolve their attack methodologies, organizations need the people, processes, and technologies that allow them to rapidly respond to a security incident. According to research, attacks have increased by 15% since 2019.
What Is Cryptojacking and How Can You Defend Against It?
The Linux process and session model as part of security alerting and monitoring
The Linux process model, available within Elastic, allows users to write very targeted alerting rules and gain deeper insight into exactly what is happening on their Linux servers and desktops. In this blog, we will provide background on the Linux process model, a key aspect of how Linux workloads are represented.
Regulatory Compliance - Holding Security Back or Forcing us to Reassess old biases?
A recent survey conducted by IBM and Censuswide of the UK market explored some of the drivers for modernisation and revealed some interesting challenges that organisations currently face as more and more businesses expand their digital boundaries.