Your guide to SaaS compliance: Key areas and best practices
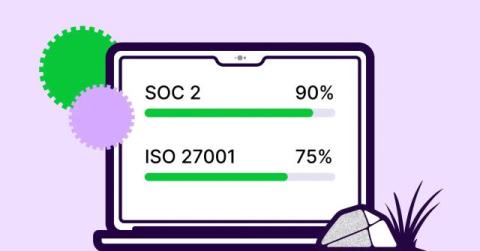
Many IT managers find compliance to be one of the most complex aspects of the SaaS space. For instance, in a LogicMonitor survey on cloud solutions, 60% of the respondents highlighted governance and compliance as one of their top challenges when engaging with SaaS platforms. SaaS compliance requires adherence to various standards and regulations that can present a recurring workload for security teams in any industry.