How to Implement Microsoft Security Products for Maximum Value
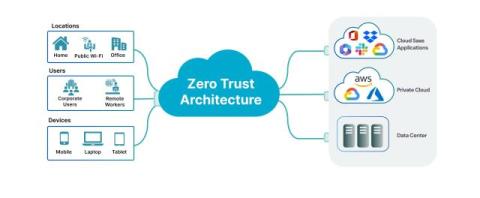
Cybersecurity teams are in a tough spot these days. They are stuck between the pace of change in technology, the shortage of security professionals, and an overabundance of security tools all demanding their attention. It's a combination that should make the all-encompassing Microsoft Security product suite a compelling idea – if you can determine a migration strategy that makes sense for your company.