CIO POV: Building Trust in Cyberspace
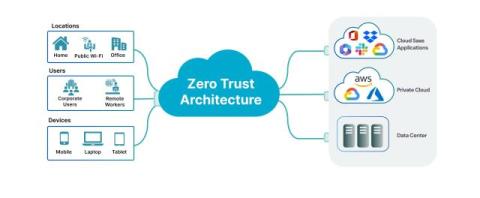
Trust lies at the heart of every relationship, transaction and encounter. Yet in cyberspace—where we work, live, learn and play—trust can become elusive. Since the dawn of the Internet nearly 50 years ago, we’ve witnessed incredible digital transformations paired with increasingly formidable threats. Knowing who and what to trust has become so difficult that the very notion of trust has been flipped on its head.