Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
The three core strengths of USM Anywhere
USM Anywhere is the ideal solution for small and mid-sized businesses that need multiple high-quality security tools in a single, unified package. There’s no reason large, global enterprises should have a monopoly on top cybersecurity technology. Solutions like USM Anywhere give smaller organizations access to security tools that are both effective and affordable.
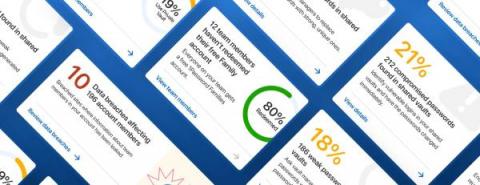
Announcing Insights from 1Password
IT and security professionals rely on one thing above all else to minimize risk: information. Today, we’re announcing a brand new way for 1Password Business customers to view their account security posture with unprecedented visibility into password health, data breaches, and team usage.
Ransomware attack vectors: what your organisation needs to look out for
OT:ICEFALL: 56 Vulnerabilities Caused by Insecure-by-Design Practices in OT
It has been 10 years since Project Basecamp, a research project conducted by Digital Bond that investigated how critical operational technology (OT) devices and protocols were, to use the term they coined, “insecure by design.” Since then, we have seen hugely impactful real-world OT malware such as Industroyer, TRITON, Industroyer2 and INCONTROLLER abusing insecure-by-design functionality.
CVE-2021-43702 from Discovery to Patch: ASUS Modem/Router Device Takeover Vulnerability
While studying for my master's degree in cyber security, I co-authored a paper regarding the rollout of IoT devices and the security considerations that businesses need to address to ensure these devices are secure. The paper underscored how a large majority of IoT devices used vulnerable components and did not follow basic secure programming principles.
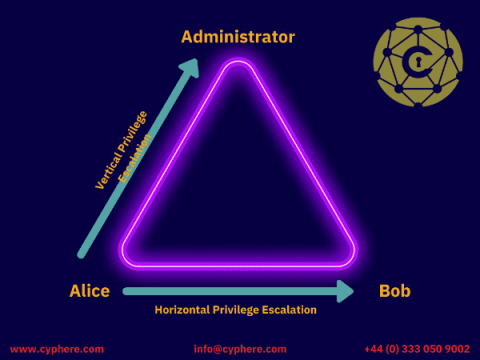
Privilege Escalation Attacks: Types, Examples and Defence
When a system is breached, compromised or exploited, the attackers never stop after getting the initial access because it doesn’t give them privileged access. And the same thing goes in an offensive security assessment, i.e. infrastructure penetration testing or a red team assessment.
Announcing the 2022 State of Open Source Security report from Snyk and the Linux Foundation
Open source software is a key component in modern applications. It has created a new era in software development, promoting a free exchange of ideas within the developer community and enabling developers to build more functional software, faster than ever. Based on most estimates, 70-90% of any piece of modern software includes open source code.
How to detect the containers' escape capabilities with Falco
Attackers use container escape techniques when they manage to control a container so the impact they can cause is much greater. This’s why it is a recurring topic in infosec and why it is so important to have tools like Falco to detect it. Container technologies rely on various features such as namespaces, cgroups, SecComp filters, and capabilities to isolate services running on the same host and apply the least privileges principle.
Uncovering the dark web: What is it and who uses it?
The dark web is the seedy underbelly of the internet. Unlike the surface web, criminals, spies, freedom fighters, and hacktivists can operate anonymously on the dark web, making it a popular place for illicit activity. Legitimate internet users also use it to protect their privacy in a world where people are increasingly mistrustful of digital giants like Google and Facebook. But it’s very easy to accidentally view illegal, dangerous, and traumatizing material on the dark web.