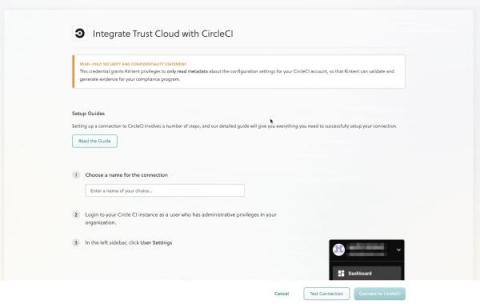
New Integrations Just Announced: CircleCI and Travis CI
Since working on a spreadsheet, you and your team have come a long way. You’re enjoying the ease of working in TrustOps because it automates control mapping, test creation, and evidence workflows. However, you’re looking for ways to save a bit more time, so you can focus on your day job and growing list of priorities. Collecting evidence to validate compliance controls takes time and affects your team’s productivity, including HR, IT, and DevOps.