Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
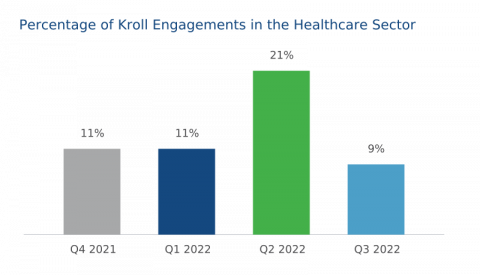
Cyber Threat Intelligence Series: A Lens on the Healthcare Sector
A review of recent Kroll incident response cases consistently proves that the healthcare industry is one of the most frequently targeted sectors. This observation mirrors what is experienced by national cybersecurity agencies as multiple warnings have been launched during 2022, highlighting how ransomware gangs and nation state actors are now aggressively targeting healthcare institutions.
Kubernetes network policy best practices
Controlling and filtering traffic when containerizing a workload within Kubernetes Pods is just as crucial as a firewall in a more traditional network setup. The difference is that, in this scenario, those capabilities are provided by the Kubernetes NetworkPolicy API. This article will explore Kubernetes NetworkPolicy by creating an example network policy and examining its core parameters. Then, we’ll look at some common NetworkPolicy use cases and learn how to monitor them using kubectl.
Seven Signs Your Digital Data Is Compromised
Personal data such as email addresses and passwords unlock our online identities and have become part and parcel of almost all accounts on the internet. Research indicates that there are over 5 billion daily web users worldwide and mobile phones account for about 60% of the world’s web traffic. Digital data examples include text messages, videos, satellite images and data from IoT, smart devices and social media.
Trustwave 2023 Cybersecurity Predictions: Part 2
In predicting what will transpire in cybersecurity in 2023, the best method is to look at past experience. As with any security and criminal activity, threat actors tend to build upon what they have done in the past, adding new twists to keep their tactics fresh and effective. So, taking this into consideration, it is no surprise that Trustwave's security experts see much of the same type of attacks that plagued 2022 continuing.
SecurityScorecard Empowers Customers to Maximize their Security Investments by Providing a One-Stop Shop with Dramatically Expanded Partner Marketplace
As demand for greater security visibility accelerates, SecurityScorecard Marketplace, the one-stop shop for trusted SecurityScorecard partner solutions, has gained significant momentum. In 2022, the Marketplace partner ecosystem expanded by 80% to now include more than 90 technology and integration partners, including OneTrust, Coupa, CSC, CrowdStrike, IBM, Splunk, and Snowflake.
Challenge Accepted: An Appointment with Dr. Zero Trust
How Can the MITRE ATT&CK Framework Help You Mitigate Cyber Attacks?
Firewall Log Management and SIEMs
Firewalls are the first line of defense in any network. Firewalls can be software or appliances, and organizations can configure them up to allow or disallow some or all IP traffic, or to verify specific traffic types based on rules that use deep packet inspection. For maximum effectiveness, it’s critical to monitor the operation of your firewalls to spot threats and misconfiguration.
What is Database Hardening and Why Is It Critical?
Hardening the various systems across your network helps you improve your cybersecurity posture level and block attacks. Hardening includes regular patching of known software vulnerabilities and turning off nonessential services on each system to reduce the number of processes that can be exploited. Hardening your database servers is a vital part of this information security strategy.