How to Keep Your Data Secure as a Digital Nomad
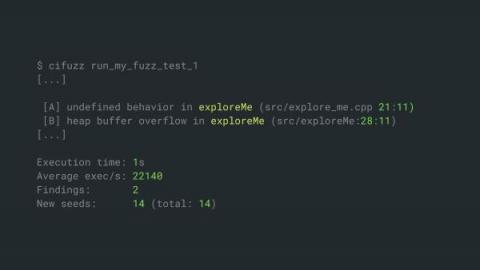
Now that remote work has become the norm, employees are taking advantage of this opportunity to travel the globe and work from anywhere in the world—as long as it’s within company policy. With the rise of digital nomads, it is important that you know how to keep yourself safe from cyberattacks when working remotely from city to city. This blog will help you understand what you need to do to secure your data as a digital nomad.