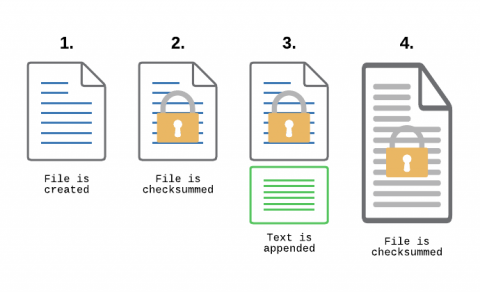
Integrity Monitoring Use Cases: Compliance
The IT ecosystems of enterprises are highly dynamic. Typically, organizations react to this volatility by investing in asset discovery and Security Configuration Management (SCM). These core controls enable businesses to compile an inventory of authorized devices and monitor the configurations of those assets. In addition to managing changes to their infrastructure, organizations must also keep an eye on the changes made to essential files.