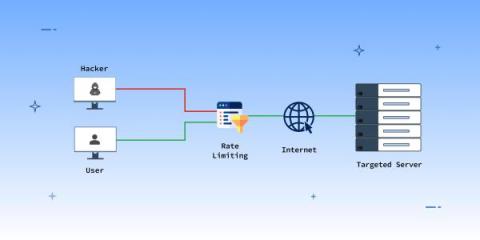
Half of U.K. Companies Have Been a Cyber Attack Victim in the Last Three Years
New data puts the spotlight on the human factor in U.K. cyber attacks, where users continue to be susceptible to social engineering, creating the so-called “Human Risk.” Here at KnowBe4, we’re obviously big believers in the fact that users are a source of risk when it comes to organizational security. Cybersecurity vendor SoSafe’s Human Risk Review 2023 report provides some independent perspective on this very problem. According to the report, one out of two U.K.