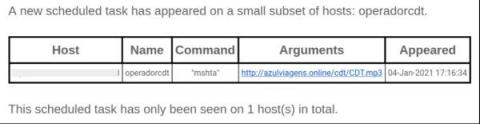
Card-Not-Present fraud (CNP): Five things retailers can do to protect themselves from CNP attacks
Cybercriminals have been well ahead of the curve when it comes to cybersecurity in the online retail industry. Specifically, criminals have been exploiting changes in purchasing behavior that favor online transactions and adapting their methods to take advantage of the authentication challenges arising when a card is not present (CNP) at the time of the transaction.