Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
November 2023
MDR vs MSSP vs SIEM: The Evolving Threat Detection Landscape
Effective threat detection is critical to achieving a mature cybersecurity posture. Yet with so many threat detection options on the market, from managed detection and response (MDR) to managed security service providers (MSSPs) to security information and event management (SIEM), choosing the most effective one for your organization can be challenging.
Getting Your Daily Security News Into Graylog
Grow Your Business with a 24/7 Security Operations Center (SOC) using Open Source Technologies.
Making the cloud the safest place to compute: Sumo Logic Cloud Infrastructure Security for AWS
Why There's No Such Thing As a Low-Cost SIEM
Staff time, log processing, and legacy issues can turn free, open-source or low-cost SIEMs into one of your organisation’s most expensive investments. You’re not alone if you’re baulking at the idea of paying upwards of tens of thousands of pounds for a new or renewed SIEM licence. Many security decision-makers feel the same way. One survey showed that almost half (40%) of existing SIEM users feel like they are overpaying for their SIEM.
Stronger Together: Protect Your Organization with the Power of the Community
Cybersecurity is a team sport, as malicious actors and advanced persistent threats are constantly evolving their tactics. In this ever-changing landscape, it is crucial for organizations to collaborate and learn from one another’s experiences. At Devo, we recognize the importance of teamwork in combating these threats. We are committed to enhancing our product capabilities and content to empower every customer to participate in this collective defense.
Maximizing security insights: A deep dive into the Amazon Security Lake and Elastic Security integration
Tech Talk Webinar - Elastic SIEM + Tines SOAR
CMMC v2 Compliance with EventSentry
Cloud SIEM Automation - Sumo Logic Customer Brown Bag - Security - November 14th, 2023
Unlocking the Power of Co-Managed SOC: A Strategic Solution for Maximizing SIEM Effectiveness and Cybersecurity Success
Security information and event management (SIEM) systems play a pivotal role in cybersecurity: they offer a unified solution for gathering and assessing alerts from a plethora of security tools, network structures, and software applications. Yet, the mere presence of a SIEM isn't a magic bullet. For optimal functionality, SIEM systems must be appropriately set up, governed, and supervised round-the-clock.
XDR vs SIEM: Cost-Efficient Cyber Security for Today's Decision Makers
CISOs and IT leaders are tasked with the critical responsibility of safeguarding their organisations against an ever-increasing array of threats, all while striving to optimise costs and drive business growth. CISOs are grappling with the demand to achieve more with limited resources this year—a challenge that many have not encountered before.
Detecting account compromise with UEBA detection packages
Valuable Career Insights for Your Career in Cybersecurity
Change is constant in any career, and the world of cybersecurity is no exception. Hackers and cybercriminals devise new tactics regularly, and cybersecurity professionals must stay current with emerging threats and new technology. While keeping pace with these shifts is essential, it’s also important to balance your commitment to the field with your personal career goals.
What's new in Elastic Security 8.11: Piped queries, AI assistance, and cloud and user data
Applying an intelligence-based approach to Cybersecurity; SIEM and dark web monitoring
“History repeatedly has demonstrated that inferior forces can win when leaders are armed with accurate intelligence.” – Central Intelligence Agency; Intelligence in War In the ever-changing landscape of global cybersecurity, the boundaries between traditional military intelligence and cybersecurity are increasingly blurred. At the heart of this convergence lies the science of intelligence analysis—a process fundamental to both realms.
Falcon Platform Raptor Release
Maximizing Data Security in the Cloud - Outperforming On Premise Solution - it-sa 2023 Keynote
Challenges with Cybersecurity Asset Identification and Management
Cloud SIEM Log Parser Templates
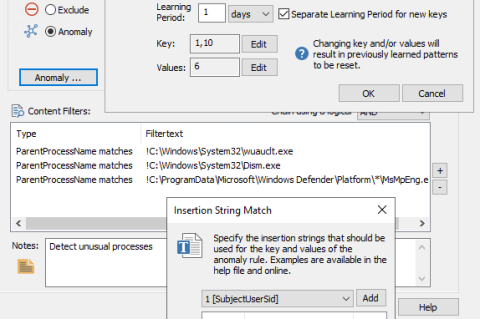
EventSentry v5.1: Anomaly Detection / Permission Inventory / Training Courses & More!
We’re extremely excited to announce the availability of the EventSentry v5.1, which will detect threats and suspicious behavior more effectively – while also providing users with additional reports and dashboards for CMMC and TISAX compliance. The usability of EventSentry was also improved across the board, making it easier to use, manage and maintain EventSentry on a day-by-day basis. We also released 60+ training videos to help you get started and take EventSentry to the next level.