Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
August 2023
The Common Cloud Misconfigurations That Lead to Cloud Data Breaches
The cloud has become the new battleground for adversary activity: CrowdStrike observed a 95% increase in cloud exploitation from 2021 to 2022 and a 288% jump in cases involving threat actors directly targeting the cloud. Defending your cloud environment requires understanding how threat actors operate: how they’re breaking in and moving laterally, which resources they target and how they evade detection.
What The Cloud? | Talk Data To Me
Automate incident response and security workflows with Blink in the Datadog Marketplace
Security and DevOps engineers often spend a lot of time and effort creating and managing complex, repetitive workflows, such as incident response, honeypotting, recovery and remediation, and more. Blink is a no-code security platform that enables users to create workflow automations, triggers, and self-service apps to streamline processes, better enforce guardrails, and eliminate operational bottlenecks.
Unveiling best practices for a resilient cloud security strategy
The transition to cloud-based environments has ushered in unparalleled efficiency, scalability, and innovation. However, it has also magnified the importance of fortifying our digital fortresses against an array of potential risks. Considering the increasing reliance on cloud computing, it’s important to find the best practices and strategies that organizations can adopt to enhance their cloud security posture and mitigate the risks associated with cloud-based environments.
From Hardware to Cloud: Modernizing IT Infrastructure for Business Success
4 Ways To Improve Your Cloud Security Posture Management
New Cloud TAP Traffic Capture for Netskope Intelligent SSE
For remote work and hybrid working environments where we are now more dispersed the central collection point for traffic captures is within the cloud. Networking, infrastructure and operations, and security teams require traffic visibility for troubleshooting, performance monitoring, threat detection, discovery of assets, and to address compliance use cases.
Unlock Secure Hybrid Cloud Excellence: Building Digital Resiliency with Secure Application Delivery
Migrating to the Cloud - How to Guarantee CFO Buy-In
If you’re keeping up with industry trends, you know the cloud is the future (and the now) of business data. 90% of companies are already on the cloud, and navigating away from an on-premise infrastructure has become a top initiative for companies worldwide to keep up with security efforts, advancements in technology, and customer demand.
Cloud-Centric Permission Management: A Conversation with Ron Nissim
In this conversation, Phillip Wylie is joined by Ron Nissim, the CEO of Entitle. They delve into the dynamic world of authentication and privilege access management, exploring the significance of automation and simplification in securing our digital landscape. They dive into the future of authorization and how innovative solutions like Entitle are reshaping the way we protect our data and systems.
How a Cloud Management Platform like OptiXdashboard Streamlines Cloud Ops
While threats of ransomware make the headlines week after week, the ability to ensure the security of data remains top of mind for enterprise leaders in every industry. While many organizations are migrating to the cloud, comprehensive control and analysis remain a priority even after leaving behind on-premise storage.
Avoid Dangerous Cloud Migration Mistakes with these 4 Tips
Unstructured data is the efficiency elephant in the room for most businesses. In fact, 95% of businesses need to manage unstructured data. Until you get a hold of the systems and process behind your data, your business is operating in the dark. A well-organized cloud environment can put your data and your business on a clear, secure footing. But, you’ll have to migrate that data from point A to point B.
AWS Security Checklist And Best Practices
At the heart of nearly every digital transformation strategy is a core focus on flexibility, scalability, and, most importantly, security. Amazon Web Services (AWS), a leader in the cloud services sector, empowers organizations to execute complex business processes while ensuring priority is given to robust AWS security practices. When you choose to move your data and applications to the cloud, security certainly takes a front-and-center role.
AWS Penetration Testing Service | Secure Your Cloud Infrastructure
Azure Cloud Security: Benefits And Best Practices
In today’s rapidly evolving digital landscape, businesses are increasingly turning to cloud solutions to power their operations, streamline processes, and drive innovation. Among the leading players in this domain, Microsoft Azure stands out as a versatile and robust cloud platform that offers a wide array of services to meet diverse business needs. However, with great power comes great responsibility, and ensuring your Azure cloud’s security is paramount.
AWS Penetration Testing - A Step-by-step Guide
AWS stands for Amazon Web Services. AWS penetration testing is the process of testing a cloud infrastructure for potential vulnerabilities. It involves identifying, exploiting and reporting security flaws that could put the system at risk. This type of test helps organisations identify and mitigate any risks to their data and applications hosted on the AWS platform and provide maximum protection for their business operations.
Azure Penetration Testing Service | Protect Your Cloud Applications Now
5 Best Tools For AWS Penetration Testing This 2023
AWS Penetration Testing is an evaluation of the security posture of a system or application to identify and mitigate potential vulnerabilities that can be exploited. It helps organisations defend against malicious attacks by identifying misconfigurations, weaknesses, and other threats in their cloud environment.
Protecting And Recovering Cloud Load Balancers
Cloud Security and Data Resilience in Government
Cloud Penetration Testing Service: Safeguarding Your Digital Fortresses
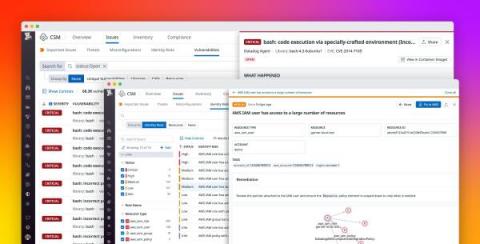
How we use Datadog CSM to improve security posture in our cloud infrastructure
In complex cloud environments where the speed of development is accelerated, managing infrastructure and resource configurations can be an overwhelming task—particularly when certifications and compliance frameworks like PCI, HIPAA, and SOC 2 present a lengthy list of requirements. DevOps and engineering teams need to ship code updates at a rapid pace, making it easy for them to accidentally overlook misconfigurations.
Three Ways to Enhance Your Cloud Security with External Attack Surface Management
The IT future is a cloudy one. Organizations are increasingly relying on cloud servers, as today’s IT environments use a combination of public and private clouds alongside on-premise infrastructure. Gartner® estimates that by 2026, 75% of organizations will adopt a digital transformation model predicated on the cloud as the fundamental underlying platform.
Spending, Security, and Expertise Are the Top 3 Cloud Challenges - But They Don't Have to Be Yours
Cloud computing has become ubiquitous in modern business, enabling organizations to store and access data and applications from anywhere. However, as the use of cloud services continues growing, so do the challenges that come with it. According to the 2023 Flexera State of the Cloud Report, security, spending, and expertise are among the top concerns for organizations leveraging cloud services.
Securing your Cloud Infrastructure with AWS
An August reading list about online security and 2023 attacks landscape
In 2023, cybersecurity continues to be in most cases a need-to-have for those who don’t want to take chances on getting caught in a cyberattack and its consequences. Attacks have gotten more sophisticated, while conflicts (online and offline, and at the same time) continue, including in Ukraine. Governments have heightened their cyber warnings and put together strategies, including around critical infrastructure (including health and education).
Application Security Report: Q2 2023
Cloudflare has a unique vantage point on the Internet. From this position, we are able to see, explore, and identify trends that would otherwise go unnoticed. In this report we are doing just that and sharing our insights into Internet-wide application security trends. This report is the third edition of our Application Security Report. The first one was published in March 2022, with the second published earlier this year in March, and this is the first to be published on a quarterly basis.
5-Step Guide on Securing Serverless Architectures in the Cloud with RASP
Serverless architecture has increased in recent years, and is anticipated to grow by nearly 25% over the next decade, According to one source, the serverless architecture market was worth over $9 billion in 2022, with its compound annual growth rate projected to increase. The market could be worth over $90 billion by 2032. This indicates the immense amount of potential that this industry carries, influenced by the increasing adoption of DevOps by organizations.
Penetration Testing in AWS: Can You Test Your Cloud Security?
AWS Security provides organisations with the tools and resources they need to protect their applications, services and data in the cloud. It can help businesses identify areas of vulnerability, detect malicious activity, monitor traffic patterns for suspicious activity and prevent unauthorised access. It includes features like encryption, authentication, risk assessment and compliance monitoring.
Changes to Datadog Cloud Security Management
In order to better meet organizations’ specific requirements for securing their environments, we are making changes to our Cloud Security Management product. On August 1, Datadog introduced new offerings in Cloud Security Management: CSM Pro and CSM Enterprise. Alongside Datadog Cloud Workload Security, these distinct packages provide customers with security capabilities tailored to their particular use cases and needs.
Securing your cloud networks: Strategies for a resilient infrastructure
What exactly is resilience? According to the U.S. National Institute of Standards and Technology, the goal of cyber resilience is to “enable mission or business objectives that depend on cyber resources to be achieved in a contested cyber environment.” In other words, when you’re at odds with cybercriminals and nation-state actors, can you still get your job done? If not, how quickly can you get back up and running?
How to revoke access for unwanted guests in Azure Active Directory
Do your house guests still have access to your home after they’ve left, or overstayed their welcome? No, right? You would throw them out or take the keys back because they no longer require access. Guests in Azure are like house guests. Once they no longer need access, it's then time to take back the key so they no longer have access to the company's data and connected apps. Yet many organizations are inadvertently leaving themselves at risk of supply chain attacks.
4 Business Advantages of the Cloud for Financial Services
Financial institutions, banks, accounting firms, credit unions, and hedge funds may struggle to stay compliant and protect themselves from cyberattacks’ rising frequency. While data security may be top of mind for financial organization teams, they can gain peace of mind and set themselves up for long-term growth by partnering with a managed cloud services provider.
Introducing Cloudflare's 2023 phishing threats report
After shutting down a ‘phishing-as-a-service’ operation that impacted thousands of victims in 43 countries, INTERPOL recently noted, “Cyberattacks such as phishing may be borderless and virtual in nature, but their impact on victims is real and devastating.” Business email compromise (BEC), a type of malware-less attack that tricks recipients into transferring funds — for example — has cost victims worldwide more than $50 billion, according to the FBI.
Combatting Cloud Threats: The Accelerated Attack Speed of 2023 (LIVE)
Penetration Testing in AWS: Can You Test Your Cloud?
AWS Security provides organisations with the tools and resources they need to protect their applications, services and data in the cloud. It can help businesses identify areas of vulnerability, detect malicious activity, monitor traffic patterns for suspicious activity and prevent unauthorised access. It includes features like encryption, authentication, risk assessment and compliance monitoring.
What's ABAC? How Attribute Based Access Control Works
Cloud Application Security: What Every Organization Needs to Know About Protecting Data in SaaS Apps
The rise of hybrid work has accelerated digital transformation for organizations of all sizes. As a result, more and more applications and data are moving to the cloud. While this has created a number of benefits — including cost savings, ease of access, and increased operational efficiencies — the cloud has also made it more challenging to protect sensitive data.
Simplify and Secure Applications Across Clouds with the Latest, High-Performance Thunder ADC Images
How to Use Google SIEM: A Complete Guide
What do you know about how to use Google SIEM? You can read about implementing these managed security services into your company's network protocols.
17 Best Cloud WAAP & WAF Software in 2023
One Drive, Double Agent: Clouded OneDrive Turns Sides
Over the past few years, ransomware has emerged as one of the most significant cybersecurity threats. Recent research conducted by Sophos indicates that the situation is becoming increasingly dire. Notably, the payments demanded by ransomware groups have surged, making the attacks even more costly for victims. Additionally, an alarming 66% of organizations have reported being targeted by ransomware attacks in the last two years alone.
Cloudflare Bot Management now on IBM Cloud Internet Services to address growing threat landscape for enterprises
Introducing per hostname TLS settings - security fit to your needs
One of the goals of Cloudflare is to give our customers the necessary knobs to enable security in a way that fits their needs. In the realm of SSL/TLS, we offer two key controls: setting the minimum TLS version, and restricting the list of supported cipher suites. Previously, these settings applied to the entire domain, resulting in an “all or nothing” effect.
The Top 5 Vendor-Neutral Cloud Security Certifications of 2023
All segments of the cloud market are predicted to see growth in 2023, according to research by Gartner. In an April Press Release, the firm forecasts that global spending on public cloud services will exceed 21% this year, totaling $597.3 billion overall in 2023. This is up over $100 billion from last year’s (mere) $491 billion.
CISO Global Receives $49 Million Valuation for Argo Edge Cloud Security Platform
Project Cybersafe Schools: Bringing security tools for free to small K-12 school districts in the US
Like other under-resourced organizations, schools face cyber attacks from malicious actors that can impact their ability to safely perform their basic function: teach children. Schools face email, phishing, and ransomware attacks that slow access and threaten leaks of confidential student data. And these attacks have real effects. In a report issued at the end of 2022, the U.S.
5 tips to supercharge app security from code to cloud
As the partnership between Snyk and GitGuardian continues to grow, we’ve collaborated on a new cheat sheet that identifies key security considerations and tools that can help you mitigate risks and protect your code. The journey from code to cloud and back to code necessitates a holistic approach to security.
Unmasking the top exploited vulnerabilities of 2022
The Cybersecurity and Infrastructure Security Agency (CISA) just released a report highlighting the most commonly exploited vulnerabilities of 2022. With our role as a reverse proxy to a large portion of the Internet, Cloudflare is in a unique position to observe how the Common Vulnerabilities and Exposures (CVEs) mentioned by CISA are being exploited on the Internet. We wanted to share a bit of what we’ve learned.
Cloud Threats Memo: Russian State-sponsored Threat Actors Increasingly Exploiting Legitimate Cloud Services
State-sponsored threat actors continue to exploit legitimate cloud services, and especially one group, the Russian APT29 (also known as Cozy Bear, Cloaked Ursa, BlueBravo, Midnight Blizzard, and formerly Nobelium), seems to be particularly active. Between March and May 2023, security researchers at Recorded Future’s Insikt Group have unearthed a cyber espionage campaign by the same threat actor allegedly targeting government-sector entities in Europe with interest in Ukraine.
Protect Your Keys - Lessons from the Azure Key Breach
Learn how to better protect your organization from attacks by looking at how attackers compromised a Microsoft signing key. Secure your keys and actively monitor code and logs.
Integrate Cloudflare Zero Trust with Datadog Cloud SIEM
Cloudflare's Zero Trust platform helps organizations map and adopt a strong security posture. This ranges from Zero Trust Network Access, a Secure Web Gateway to help filter traffic, to Cloud Access Security Broker and Data Loss Prevention to protect data in transit and in the cloud. Customers use Cloudflare to verify, isolate, and inspect all devices managed by IT. Our composable, in-line solutions offer a simplified approach to security and a comprehensive set of logs.
The Cloud Security Layer Cake: Modern Use Cases for PAM
Warm. Rich. Chocolatey. The way I see it, a proper chocolate layer cake is the best sensory experience a human can have. Let’s go a bit further still: good chocolate cake is the height of human achievement. In the world of enterprise IT, one could say the same of a diverse, purpose-built IT infrastructure. Every enterprise application – whether internal or customer-facing – must run on the right server, virtual machine (VM), container or database for the task at hand.
Mitigate identity risks and infrastructure vulnerabilities with Datadog Cloud Security Management
Cloud environments comprise hundreds of thousands of individual components, from infrastructure-level containers and hosts to access-level user and cloud accounts. With this level of complexity, it’s important to establish and maintain end-to-end visibility into your environment for many reasons—not least among them to efficiently identify, prioritize, and mitigate security threats.
2023 Global Cloud Threat Report: Cloud Attacks are Lightning Fast
The second annual threat report from the Sysdig Threat Research Team (Sysdig TRT) is packed with their findings and analysis of some of the hottest and most important cybersecurity topics this year. Threat actors are really embracing the cloud and are using it to their advantage to evade detection and speed up their attacks.
Using Asset Management to Keep a Cloud Environment Secure
In modern network environments focused on cloud technology, organizations have undergone a significant transformation in the development and deployment of their IT assets. The introduction of cloud technology has simplified and expedited the deployment process, but it often lacks centralized change management. The cloud's shared responsibility model enables quick deployment and scaling but can pose security risks if not properly managed and understood.