Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
April 2023
Cloud detection and response, a key asset for cloud security
Cloud security 101: Understanding and defending your cloud infrastructure
Many organizations have either been formed in, or have migrated to cloud-based environments due to the efficiency, flexibility, mobility, cost savings, and other benefits. The majority of applications that are used today are incorporated with the cloud. Most of our data and processes exist in the cloud. But simple as it is, just uploading your files to the cloud or using services of the cloud, doesn`t guarantee that it`s secure.
Accelerate Your Security Transformation with Google Workspace and CrowdStrike
Each day, enterprise and public sector IT teams face new challenges when managing hybrid work for networks of hundreds, or even thousands, of users. A more distributed workforce means an increased reliance on collaboration and productivity tools. It also requires a strong strategy to protect these systems against vulnerabilities and modern cyberattacks.
Improving software supply chain security for cloud applications and workloads
Uncovering Digital Evidence: Navigating the Complexities of Cloud Computing Forensic Science
Forensic investigators must understand how to navigate challenges to successfully uncover digital evidence in the cloud. By following best practices and utilizing the latest tools and techniques, organizations can be better prepared to investigate cyber threats and mitigate risks.
Cloud Threats Memo: Threat Actors Increasingly Exploiting Google Drive
Google Drive continues to be one of the most abused cloud services by threat actors, and the latest edition (April 2023) of the Threat Horizons Report, released by security researchers in Google’s Threat Analysis Group (TAG), shows more interesting examples of how opportunistic and state-sponsored threat actors are exploiting its flagship cloud storage service, to conduct malicious campaigns (and by the way, Netskope Cloud and Threat Report is quoted in the report).
Vanta has joined the AWS ISV Accelerate Program
Today I’m excited to share the latest milestone in our growing partner ecosystem: Vanta has joined the Amazon Web Services (AWS) Independent Software Vendor (ISV) Accelerate Program. The AWS ISV Accelerate Program is a co-sell program for AWS Partners who provide software solutions that run on or integrate with AWS. Vanta’s acceptance into the program enables us to work in close collaboration with the AWS sales team to meet customer needs and provide better outcomes.
Secure by default: recommendations from the CISA's newest guide, and how Cloudflare follows these principles to keep you secure
When you buy a new house, you shouldn’t have to worry that everyone in the city can unlock your front door with a universal key before you change the lock. You also shouldn’t have to walk around the house with a screwdriver and tighten the window locks and back door so that intruders can’t pry them open.
Microsoft 365 Security Series - Using Azure Active Directory to secure your Microsoft 365 Installation
Microsoft 365 (formerly Office 365) is a Software-as-a-Service (SaaS) that offers a cloud-based version of its popular software productivity suite, including MS Word, Excel, PowerPoint, Outlook, and OneNote. In contrast, Azure Active Directory (Azure AD) is an Infrastructure-as-a-Service (IaaS) that offers a cloud-based version of Active Directory to control identity management and access to virtual resources across an organization.
Consider Protegrity For Your Cloud Security
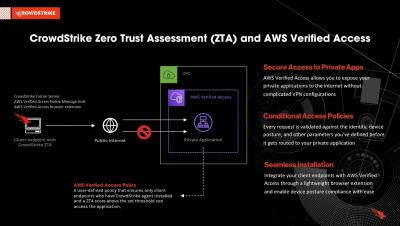
Securing private applications with CrowdStrike Zero Trust Assessment and AWS Verified Access
Securing private applications with CrowdStrike Zero Trust Assessment and AWS Verified Access
AWS Verified Access (AVA), a feature of Amazon Virtual Private Cloud (VPC) networking, delivers secure, zero-trust access to private applications without a VPN by continuously evaluating each request in real time based on contextual security signals like identity, device security status and location. The service grants access based on the security policy configured for each application and then connects the users, thereby improving the security posture of the organization.
The 443 Podcast, Ep. 236 - Another Software Supply Chain Attack
Mend.io Achieves AWS Security Competency Status
We’re delighted to announce that Mend.io has achieved Amazon Web Services (AWS) Security Competency status. This designation recognizes that Mend.io has demonstrated proven technology and deep expertise to help customers achieve cloud security goals. It reinforces Mend.io’s position as a trusted member of the AWS Partner Network (APN), which has already been established since we achieved AWS DevOps Competency status.
Securing private applications with CrowdStrike and AWS Verified Access
Cloud Identity Security: It Doesn't Taste Like Chicken
There’s a scene in the original “Matrix” movie when Neo is sitting in the grimy kitchen with the rest of the crew and eating gray, runny slop. No matter what new version of gray slop they eat, they always seem to think that it tastes like chicken. When confronted with something new, it’s a natural human trait to relate it back to something we already know.
Effective AWS Incident Response: Examples and Recommendations
The use of Amazon Web Services (AWS) in organizations around the world is prolific. The platform accounted for 31% of total cloud infrastructure services spend in Q2 2022, growing by 33% annually. Despite its widespread use, many organizations still fail to consider the nuances of incident response in AWS.
Cloud forensics - An introduction to investigating security incidents in AWS, Azure and GCP
The cloud has revolutionized the way we do business. It has made it possible for us to store and access data from anywhere in the world, and it has also made it possible for us to scale our businesses up or down as needed. However, the cloud also brings with it new challenges. One of the biggest challenges is just keeping track of all of the data that is stored in the cloud. This can make it difficult to identify and respond to security incidents.
Detectify's journey to an AWS multi-account strategy
In the past year, we’ve shifted our infrastructure from a single Amazon Web Services (AWS) account owned by our Platform team to multiple domain-specific accounts. For each product domain and environment, we have created AWS accounts, which has allowed us to improve stability and security by reducing the blast radius. This setup also provides excellent scalability with good cost observability across the organization.
Netskope named a Leader in the Gartner Magic Quadrant for Security Service Edge (SSE)
Cloudflare One named in Gartner Magic Quadrant for Security Service Edge
Gartner has recognized Cloudflare in the 2023 “Gartner® Magic Quadrant™ for Security Service Edge (SSE)” report for its ability to execute and completeness of vision. We are excited to share that the Cloudflare Zero Trust solution, part of our Cloudflare One platform, is one of only ten vendors recognized in the report. Of the 10 companies named to this year’s Gartner® Magic Quadrant™ report, Cloudflare is the only new vendor addition.
Chaos in the Cloud: Rampant Cloud Activity Requires Modern Protection
Digital transformation isn’t only for the good guys. Adversaries are undergoing their own digital transformation to exploit modern IT infrastructures — a trend we’re seeing play out in real time as they increasingly adapt their knowledge and tradecraft to exploit cloud environments. According to the CrowdStrike 2023 Global Threat Report, observed cloud exploitation cases grew by 95% over the previous year.
Improving cloud security posture with infrastructure-as-code
Best practices for identity and access management in cloud-native infrastructure
Editor’s note: This is the final part of a five-part cloud security series that covers protecting an organization’s network perimeter, endpoints, application code, sensitive data, and service and user accounts from threats. So far in this series, we’ve looked at the importance of securing an organization’s network, its application components, the endpoints that support those components, and its application data.
Customize rules for detecting cloud misconfigurations with Datadog Cloud Security Management
For organizations in highly regulated industries, any misconfiguration in their cloud environments can be detrimental to customer trust and privacy if overlooked. To mitigate this risk, DevOps and security engineers follow recognized compliance standards to quickly surface issues in their AWS, Azure, or Google Cloud environments. Organizations can take this work a step further by developing detection rules tailored to their unique business or security goals.
1- Introducing Zaraz
2 - How Zaraz Works
3 - Introduction to Cloudflare
4 - How to Install Zaraz
5 - Zaraz Web API
6 - Zaraz Vs Google Tag Manager GTM
7 - How to Configure Zaraz
8 - Advanced
9 - Testing & Debugging
10 - Consent Management & Privacy
11 - Managed Components (MC)
Real-time co-editing on desktop using native Google Workspace tools
With deep integrations into Google Workspace, Egnyte enables users to streamline the document creation process by delivering a seamless experience to create, co-edit and share documents directly from within the Egnyte Desktop App and Web UI. By using Egnyte as the document source, files are also protected from internal misuse and external threats, ensuring that users can collaborate with confidence, without concerns of exposing sensitive data.
Demystifying Elastic Security for Cloud and its capabilities
How SD-WAN and Public Cloud have changed the dynamics when it comes to modern connectivity and infrastructure requirements
Digital and cloud transformation has unlocked new business opportunities and operational efficiencies for organisations. But migration to the cloud also means our approach to deploying applications and services has radically changed, as enterprises move away from traditional data centres. Likewise, flexible working means users have also moved away from traditional offices and branches.
Fix cloud security issues faster and at the source with Snyk Cloud
In July 2022, we announced Snyk Cloud, extending the Snyk developer security platform to secure application and infrastructure configurations in running cloud environments. Today, we’re thrilled to introduce a new feature of Snyk Cloud that enables you to "fix cloud issues in IaC" (infrastructure as code), making Snyk Cloud the first solution to secure the cloud through code with remediation paths in IaC.
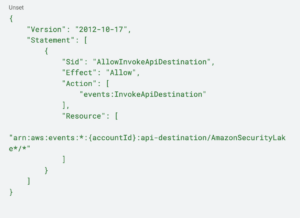
Building Efficient SecOps Pipelines with AWS Security Lake and Torq
What You Need to Know About the Netskope Accelerator Package for Azure
Over its history Netskope has delivered many tools to integrate its various solutions and findings with Microsoft products. We have built multiple integrations with Azure Active Directory, Azure Sentinel, Azure Monitor, and Azure Blob and Compute. All of these are very helpful in unlocking base or advanced functionality to augment Microsoft solutions.
Random but Memorable - Episode 10.5: Ban Cloud Fan Fiction with Stu Hirst from Trustpilot
Banks are leveraging modern cloud security tools to mitigate human error
Elastic Expands Cloud Security Capabilities for AWS
Data sovereignty in the cloud: A Canadian perspective
Cloud computing has made its way to organizations’ IT infrastructure strategy rapidly over the past few years. In particular, Canadian businesses are showing an increased adoption. This article decodes how Canada’s IT infrastructure shaped up in the last decade, why data sovereignty is now a hot topic, and what the future holds for the cloud. While on-premises IT infrastructure continues to be relevant even today, both SMBs and enterprises are now embracing the cloud more than ever.
Recap: Stress-Free Security for Devs and Ops on AWS
Snyk recently hosted a half-day virtual event focused on security for application workloads running on AWS (you can catch it on demand here). The event was broken into six sessions spanning topics like developer challenges in cloud-native AppDev, top vulnerabilities from last year, hands-on workshops with industry-leading technology vendors, and several other subjects that help enable engineering and security teams to build a successful DevSecOps workflow.