Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
March 2023
Effective Cloud Incident Response: Fundamentals and Key Considerations
Human error behind misconfigurations, a host of insecure remote access issues, exposed business credentials with reused passwords and unpatched vulnerabilities have all contributed to a significant increase in cloud security incidents. Many organizations don’t foresee the challenges of what it will take to protect their data and operations after a move to the cloud.
Helping protect personal information in the cloud, all across the world
Cloudflare has achieved a new EU Cloud Code of Conduct privacy validation, demonstrating GDPR compliance to strengthen trust in cloud services.
Elevate your AWS Experience: Unleash the Power of Veeam BaaS with David Johnson and Sagi Brody
CTI Roundup: New CISA tool detects hacking activity in Microsoft cloud services
A joint advisory on LockBit 3.0 ransomware, CISA’s latest tool which detects hacking activity in Microsoft cloud services, and ScarCruft’s evolving arsenal.
How to Detect SCARLETEEL with Sysdig Secure
The recent SCARLETEEL incident highlights the importance of detecting security threats early in the development cycle. With Terraform state files, attackers can easily access sensitive information and gain unauthorized access to your cloud infrastructure. In this case, the attackers exploited a containerized workload and used it to perform privilege escalation into an AWS account, stealing software and credentials.
Understanding the Basics of Cloud Security: API Security for Dummies
It’s no exaggeration to say that APIs are the backbone of the modern digital economy. API usage has seen staggering exponential growth over the last two decades with sources like Postman's 2022 State of the API Report illustrating just how embedded APIs are into our modern world. In 2022, the Postman API platform saw 20 million users and over 1 billion API requests created.
AWS in 30 recap
Last month, Lead Partner Solutions Architect, David Schott, presented a demo on how Snyk works alongside Amazon Web Services (AWS) to identify vulnerabilities at every level of development and infrastructure. David covered why agile development in the cloud requires a different security approach than simply using the IT security methods of the past. Then, he showed a real-time example of how Snyk’s AWS cloud security tools can find and mitigate common vulnerabilities.
SANS Cloud-Native Application Protection Platforms (CNAPP) Buyers Guide
The SANS Cloud-Native Application Protection Platforms (CNAPPs) Buyers Guide gives companies a deep dive into what to look for in a CNAPP solution. As organizations continue to shift towards integrated platform-based solutions for their cloud security needs, it becomes critical to evaluate whether a CNAPP solution meets all the requirements across use cases like posture management, permissions management, vulnerability management, and threat detection and response.
Cloudflare Cache Reserve Walkthrough and Demo
The Shift to the Cloud and its Implications for Application Security
Everybody’s doing it: shifting applications to the cloud. More flexibility. More storage. More scalability. But how does this affect application security? What challenges does it present?
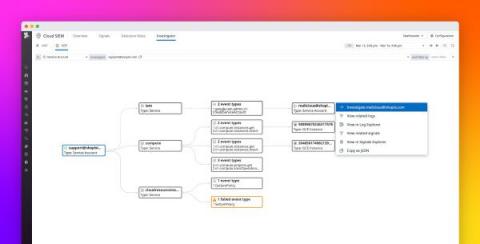
Visualize activity in your Google Cloud environment with Datadog Cloud SIEM Investigator
Cloud environments, in all their dynamic complexity, demand careful monitoring by DevOps and security teams. But the sheer abundance of telemetry data associated with the thousands of resources, users, and roles that comprise these environments can make monitoring a formidable task, causing security risks and other issues to be all too easily overlooked.
Netskope Modern DLP
How to Handle AWS Secrets
In this blog post, we'll cover some best practices for managing AWS secrets when using the AWS SDK in Python.
Top 6 Cloud Insider Threats You Need To Be Aware Of
Cloud computing is the most cost-effective way to store and manage data and meet growing business demands today. However, the rapid rise of cloud usage means you need to stay alert to potential cloud security insider threats that can compromise your sensitive data and security posture. In this post, we discuss the insider threat landscape, explore several types of cloud insider threats, and examine the best practices to combat these threats.
Everything you might have missed during Security Week 2023
Security Week 2023 is officially in the books. In our welcome post last Saturday, I talked about Cloudflare’s years-long evolution from protecting websites, to protecting applications, to protecting people. Our goal this week was to help our customers solve a broader range of problems, reduce external points of vulnerability, and make their jobs easier. We announced 34 new tools and integrations that will do just that.
Account Security Analytics and Events: better visibility over all domains
Cloudflare offers many security features like WAF, Bot management, DDoS, Zero Trust, and more! This suite of products are offered in the form of rules to give basic protection against common vulnerability attacks. These rules are usually configured and monitored per domain, which is very simple when we talk about one, two, maybe three domains (or what we call in Cloudflare’s terms, “zones”).
Wildcard and multi-hostname support in Cloudflare Access
We are thrilled to announce the full support of wildcard and multi-hostname application definitions in Cloudflare Access. Until now, Access had limitations that restricted it to a single hostname or a limited set of wildcards. Before diving into these new features let’s review Cloudflare Access and its previous limitations around application definition.
Why CNAPP Needs Runtime Insights to Shift Left and Shield Right
There’s an important shift happening in the cloud security industry: organizations are looking for an integrated platform that connects the dots between several key security use cases from source through production. Whether it is for tool consolidation, consistent end-to-end experience, or “one throat to choke,” customers are increasingly choosing a platform-based approach to address critical cloud security risks.
Cloudflare Access is the fastest Zero Trust proxy
During every Innovation Week, Cloudflare looks at our network’s performance versus our competitors. In past weeks, we’ve focused on how much faster we are compared to reverse proxies like Akamai, or platforms that sell serverless compute that compares to our Supercloud, like Fastly and AWS. This week, we’d like to provide an update on how we compare to other reverse proxies as well as an update to our application services security product comparison against Zscaler and Netskope.
Key Considerations for Building a Successful Cloud Security Program
I recently had the pleasure of participating in a great panel discussion at the San Diego Cyber Security Summit, entitled “Cloud Security — Leveraging Its Strengths and Overcoming Its Vulnerabilities,” alongside representatives from Palo Alto Networks, Gigamon, Sysdig, Lacework, Imperva, and Tufin.
Understanding Data Protection Needs in a Cloud-enabled Hybrid Work World
Today, Netskope partnered with the Cloud Security Alliance to release the Data Loss Prevention (DLP) and Data Security Survey Report, a survey focused on data protection needs in cloud and hybrid work environments. Unsurprisingly, the report found that the biggest pain point organizations identify with trying to modernize their data protection strategy is that current DLP deployments show limitations when it comes to cloud and remote work use cases, and they are a nightmare to manage.
AWS top 10 misconfigurations and how to fix them: A cheat sheet
Amazon Web Services (AWS) remains the dominant cloud provider, with 40.8% of the market share. Many enterprises and organizations today have some, if not most, of their infrastructure on Amazon Web Services. AWS helps organizations accelerate their digital transformations and innovate faster, but there are common misconfigurations when moving to AWS.
Why Companies Still Struggle with Least Privilege in the Cloud
Vulnerabilities are only one part of the cloud security story. Misconfigurations are still the biggest player in security incidents and, therefore, should be one of the greatest causes for concern in organizations.
Cloud Threats Memo: Cyber Espionage Campaign Using Remote Access Tools
Another day, another cyber espionage campaign exploiting two legitimate and well-known cloud services to deliver the malicious payload. Once again, this campaign was unearthed by researchers at Sentinel One, and it is aimed to distribute the Remcos Remote Access Tool (yet another example of a remote control tool used for malicious purposes) through the DBatLoader to target predominantly organizations in Eastern Europe.
Opti9tech Hybrid Cloud Solutions for Credit Unions
Opti9tech Cloud Operations
Opti9 Cloud Backups
OptiXdashboard Hybrid Cloud Management Tool
Opti9 Cloud Strategy - Services Built From Expertise and Experience, Customer-Centric Solutions
Opti9 and Arpio Webinar: Automated Resilience for AWS Workloads
OptiXdashboard Cloud Management Tool - Manage Your Cloud Infrastructure with a Single Platform
Realizing the True Power of Netskope Cloud Exchange
When I talk to customers and partners about Cloud Threat Exchange (CTE), I immediately say, “I’m not in marketing, and didn’t see the future—so I misnamed the module. I should have named it Cloud Data Exchange.” Why do I say this? Because, as Netskope and Cloud Exchange have matured, the number of use cases the module can fulfill has naturally grown beyond the initial vision. How so?
ARMO adds CIS EKS benchmark
How To Setup Velero Backups On EKS Using IAM Roles for Service Accounts (IRSA)
Velero is an open-source tool that allows you to backup and restore your Kubernetes cluster resources and persistent volumes. Velero backups support a number of different storage providers including AWS S3. The process of setting up Velero backup with S3 using AWS credentials has been documented by Velero here. However, at the time of this post, there is no official documentation on how to set up Velero using IRSA or IAM Roles for Service Accounts.
Mend & AWS CodeCatalyst Integration
How to get started with Cloudflare R2
Account Takeover Vulnerability in Azure's API Management Developer Portal
How an Account Takeover vulnerability, discovered during a routine customer engagement, became a candidate for responsible disclosure, via the Microsoft Security Research Center Researcher Portal.
GitGuardian Code Security Platform Now Available on AWS Marketplace
With GitGuardian available on AWS Marketplace, we’re making it easier for all organizations using AWS to protect their software supply chain from exposed secrets and credentials.
What is Cloudflare Argo Smart Routing?
Cloud Threats Memo: Multiple Different Cloud Apps Abused in a Single Cyber Espionage Campaign
Threat actors continue to exploit cloud services for cyber espionage, and a new campaign by a threat cluster named WIP26, discovered recently by researchers at Sentinel One in collaboration with QGroup, targeting telecommunication providers in the Middle East, confirms this trend.
Securing Your Amazon S3 Buckets
Amazon Web Services (AWS) is the world’s largest cloud provider, with well over a million active users. The popularity of AWS makes it one of the biggest targets for cybercriminals — and one of the leading contributors to breaches is incorrectly configured Amazon S3 buckets. For example, an insecure bucket led to the unauthorized access of 23 million documents and 6.5 TB of data belonging to Pegasus Airlines.
MITRE ATT&CK and D3FEND for Cloud and Containers
MITRE ATT&CK and MITRE D3FEND are both frameworks developed by the non-profit organization MITRE, but they serve different purposes. If you are new to the MITRE ATT&CK framework and would like to brush up on some of the concepts first, we created a Learn Cloud Native article to help you on your journey. If you want to go further, here’s how Falco’s Cloudtrail rules align with MITRE ATT&CK.