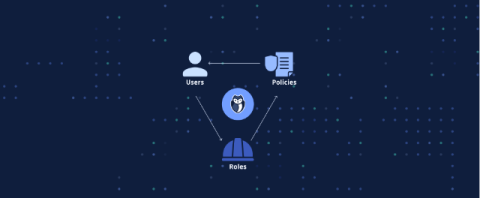
Password Policy Configuration for Safer Security
A password policy is a set of rules that are usually a part of an organizations security regulations to improve computer security. These policies can be formal regulations or part of security awareness training programs that outline requirements such as minimum length, complexity and unique characters. A password must comply with these password strength rules to be set for an account.