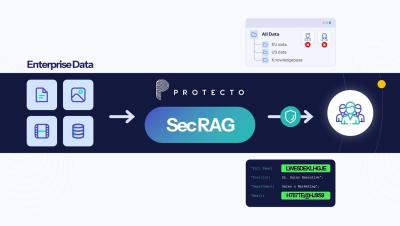
Unlocking Cyber Resilience: UK's NCSC Drafts Code of Practice to Elevate Cybersecurity Governance in UK Businesses
In late January, the UK’s National Cyber Security Centre (NCSC) issued the draft of its Code of Practice on Cybersecurity Governance. The document's goal is to raise the profile of cyber issues with organizational directors and senior leaders and encourage them to shore up their defenses from cyber threats.