Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
February 2024
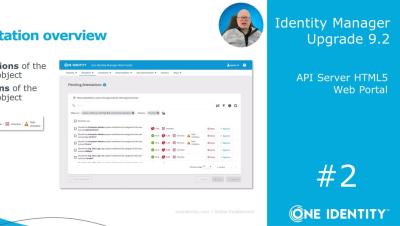
Identity Manager | Upgrade 9.2 #2 | API Server HTML5 Web Portal
Training Video Series: Identity Manager - Upgrade 9.2 API Server HTML5 Web Portal.
A Guide to Cloud Security Posture Management (CSPM)
What is CSPM? Cloud Security Posture Management is about identifying and remediating security misconfigurations and risks to (IaaS) Infrastructure as a Service or (PaaS) Platform as a service environments.
WEF Is Waging War on Misinformation and Cyber Insecurity
What is the greatest cyber risk in the world right now? Ransomware? Business Email Compromise? Maybe AI? Well, the last one is pretty close. According to the World Economic Forum, misinformation and disinformation are the most severe global risks of the next two years. In their Global Risks Report 2024, the WEF posited that the post-pandemic world is at a "turning point," with the two key problems possessing the power to do everything, from challenging mental health to eroding human rights.
What We Learned from the 2024 State of Cybersecurity Survey
Cybersecurity is a pressing topic of concern for most organizations today, as any amount of sensitive data or digital assets can present a security risk. Understanding the digital landscape, threat trends, and the way they change over time is an essential step in defending against cyberattacks. It can be daunting for any organization to stay in the loop and maintain perspective on cyberthreats and security practices.
New Research: Ransomware Incidents Spike 84% in 2023
Newly-released data covering cyberthreats experienced in 2023 sheds some light on how very different last year was and paints a picture of what to expect of cyber attacks in 2024. As someone who looks a lot at industry data, I really want it to be as relevant as possible. But it’s also important to see the larger trends over the recent past to begin to predict what’s to come.
Game-Changer: Biometric-Stealing Malware
I have been working in cybersecurity for a long time, since 1987, over 35 years. And, surprisingly to many readers/observers, I often say I have not seen anything new in the hacker/malware space since I began. The same threats that were a problem then are the same problems now. Social engineering and unpatched software (and firmware) have long been the two biggest initial root causes for hacking…for decades.
When Threat Actors Don't Have a Viable Email Platform to Phish From, They Just Steal Yours
New analysis of a phishing campaign shows how cybercriminals use brand impersonation of the platforms they need to compromise accounts and takeover legitimate services. Every day there seems to be a new term for yet another creative attack technique. The latest is phishception (a play on words from the movie Inception) coined by security analysts at cybersecurity company Netcraft.
Credential Theft Is Mostly Due To Phishing
According to IBM X-Force’s latest Threat Intelligence Index, 30% of all cyber incidents in 2023 involved abuse of valid credentials. X-Force’s report stated that abuse of valid credentials exceeded phishing as a top threat for the first time. I love IBM, but they are mixing up root causes and outcomes of root causes. What I mean is that you have to ask yourself how the credentials were stolen in the first place. Were they stolen from the user or a website? Were they guessed at?
Get the AT&T Cybersecurity Insights Report: Focus on Energy and Utilities
We’re pleased to announce the availability of the 2023 AT&T Cybersecurity Insights Report: Focus on Energy and Utilities. The report examines the edge ecosystem, surveying energy and utilities IT leaders from around the world, and provides benchmarks for assessing your edge computing plans. This is the 12th edition of our vendor-neutral and forward-looking report.
7 Smart Steps to Run Serverless Containers on Kubernetes
Serverless containers mark a notable evolution from traditional containerization. Traditional containers, being continuously active, can lead to resource wastage. Serverless containers, however, are ephemeral and operate on-demand. For developers, this means less time spent on server management and more on coding. Kubernetes, or K8s, stands out in automating, scaling, and managing these containerized applications.
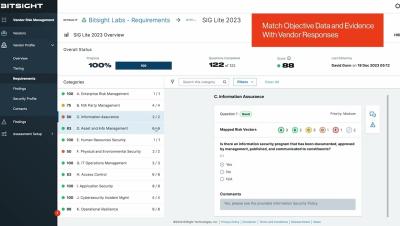
Bitsight Vendor Risk Management Walkthrough
Streamline Assessments, Monitor Vendors, and Validate Security Posture with Ease. No more manual workflows or toggling between tools—with Bitsight VRM, part of the industry’s first end-to-end third-party risk management solution, you can effortlessly navigate through risk assessments and continuous monitoring with just a flip of a switch. Discover a new level of clarity and efficiency with instant access to an ever-growing network of 40,000+ vendor profiles. Track onboarding and validate questionnaire responses with objective data to make informed decisions and expedite risk mitigation.