Introduction to Cloud Risk Management for Enterprises
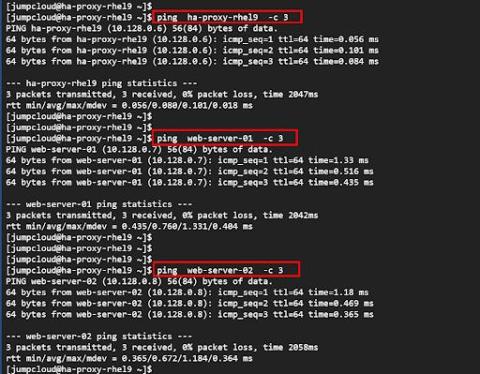
Every business needs to manage risks. If not, they won’t be around for long. The same is true in cloud computing. As more companies move their resources to the cloud, they must ensure efficient risk management to achieve resilience, availability, and integrity. Yes, moving to the cloud offers more advantages than on-premise environments. But, enterprises must remain meticulous because they have too much to lose.