Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
February 2024
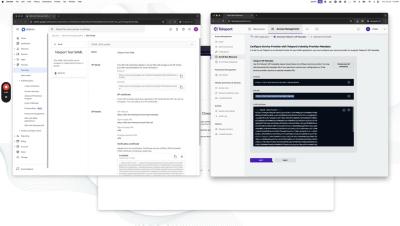
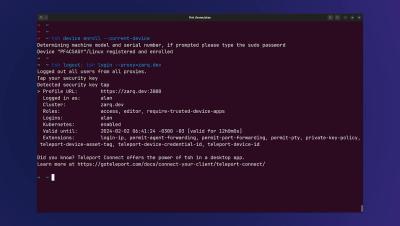
Teleport Device Trust for Linux
An overview of Teleport Device Trust for Linux, a new feature added in Teleport 15.
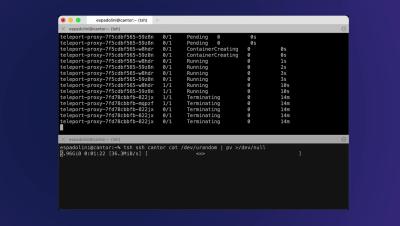
SSH connection resumption
SSH connection resumption Teleport v15 introduces automatic SSH connection resumption if the network path between the client and the Teleport node is interrupted due to connectivity issues, and transparent connection migration if the control plane is gracefully upgraded. The feature is active by default when a v15 client (tsh, OpenSSH or PuTTY configured by tsh config, or Teleport Connect) connects to a v15 Teleport node.
Cryptocurrency on the Underground
Over the past decade, cryptocurrency has significantly disrupted the economic and business landscape. Its popularity has soared, driven by the promise of anonymous transactions and the potential for substantial returns on investment. However, the crypto market’s vulnerabilities, coupled with limited government oversight, have provided fertile ground for cybercrime to flourish.
FIPS 199 & 200 Compliance: Comparing Security Standards
In the world of government contracting, information security is taken very seriously. There are a dozen different standards for security depending on who you are, what information you handle, and what department you’re working with. We’ve talked about many of them before, such as DFARS, FedRAMP, and CMMC, but there’s yet another to discuss. As you’ve guessed, if you’ve read the title, or as you know from seeing this post, we’re talking about FIPS.
Top 11 Website Security Software Solutions for 2024
It’s surprising how much website security today is often lacking, even across major and popular sites. Needless to say, such security gaps leave businesses vulnerable to hackers, viruses, and other cyber threats. Consider this: A recent brand impersonation fraud campaign targeted over 100 popular apparel brands with a vast network of 3,000+ spoofed brand websites.
Microsoft Azure Administrator: AZ-104: Manage Costs in Microsoft Azure - Part 18
A critical area of concern for organizations migrating to the cloud is cost. While cloud services have many benefits regarding management, features, and capabilities, without proper cost management, the spend can skyrocket. For the AZ-104 exam and as a Microsoft Azure Administrator, it’s crucial to grasp how cost management tools help identify and implement cost-saving opportunities. Let’s look at how we can manage costs effectively and the tools available, including Azure Cost Management.
What you can't do with Kubernetes network policies (unless you use Calico): The ability to log network security events
In my previous blog post, What you can’t do with Kubernetes network policies (unless you use Calico): Advanced policy querying & reachability tooling, I talked about this use case from the list of nine things you cannot implement using basic Kubernetes network policy — advanced policy querying and reachability tooling. In this blog post, we’ll focus on the use case — the ability to log and analyze network security events.
Exploring LLM Hallucinations - Insights from the Cisco Research LLM Factuality/Hallucination Summit
LLMs have many impressive business applications. But a significant challenge remains - how can we detect and mitigate LLM hallucinations? Cisco Research hosted a virtual summit to explore current research in the LLM factuality and hallucination space. The session includes presentations from University professors collaborating with the Cisco Research team, including William Wang (UCSB), Kai Shu (IIT), Danqi Chen (Princeton), and Huan Sun (Ohio State).
3 2 1... Impact! Early Results under the SEC's Cybersecurity Governance Rule
In July 2023, the SEC adopted a new rule requiring disclosure of “material” cybersecurity incidents and detailed information on cybersecurity risk management, strategy and governance by public companies. With the new rule taking effect in December and annual reports due for public release and consumption in the first few months 2024, companies are scrambling to closely review and hone their cyber programs to address these new reporting requirements.
Beating LockBit at its Own Game: Law enforcement's takedown of a prolific ransomware group
After a years-long investigation, this week the FBI and law enforcement agencies in the UK and Europe took over the main website of the cybercrime group known as LockBit. Law enforcement additionally arrested LockBit associates in Poland, Ukraine, and the U.S. and the U.S. Treasury imposed sanctions on Russian nationals affiliated with the group. The joint operation re-engineered LockBit’s online system to mimic the countdown clock used by the group in its extortion attempts.
Top 10 Cybersecurity Questions to Ask Your Vendors: A step-by-step guide to reduce supply chain risk
A cybersecurity vendor questionnaire is vital in assessing the competency and reliability of potential partners. It serves as a comprehensive tool to evaluate various aspects crucial for safeguarding sensitive data and infrastructure. Through detailed inquiries about security protocols, compliance measures, incident response plans, and past breach incidents, the questionnaire helps gauge the vendor’s commitment to robust cybersecurity practices.