AWS KMS Integration for Teleport
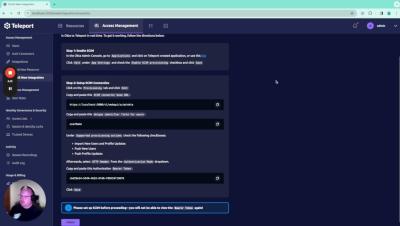
AWS KMS integration for Teleport. With this feature, we can now store cryptographic key pairs in AWS KMS, enhancing our security posture. I'll show you how to set it up for a new cluster and explain the benefits. No action is required from you, but it's important to be aware of this new capability. Let's dive in!