Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Threat Detection
Why are organizations failing to detect cybersecurity threats?
With the changing security landscape, the most daunting task for the CISO and CIO is to fight an ongoing battle against hackers and cybercriminals. Bad actors stay ahead of the defenders and are always looking to find new vulnerabilities and loopholes to exploit and enter the business network. Failing to address these threats promptly can have catastrophic consequences for the organization.
Turning the tables on the infiltrator
What happens at the point in time when an organization’s information security is compromised? This blog explores an important paradigm shift that occurs at the very moment of compromise and that can be leveraged to turn the tables on the attackers.
Black Hat NOC USA 2023: Five takeaways for SOC teams
During this year’s Black Hat in Las Vegas, I learned (or was reminded of) many lessons working alongside my Corelight colleagues and Black Hat Network Operations Center (NOC) teammates from Arista, Cisco, Lumen, NetWitness and Palo Alto Networks. The uniqueness of standing up a full security stack and NOC in such a short time with a team that comes together infrequently really forced me to consider how team processes and communication affect NOC/SOC efficiency and effectiveness.
Enhance your search experience within Splunk by using the Corelight App
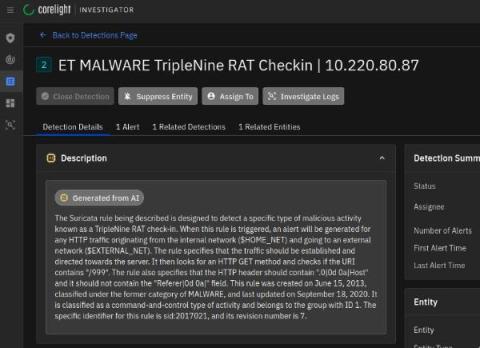
The Corelight App for Splunk provides the foundation for organizations to boost SOC effectiveness and productivity by using Corelight data in Splunk. In this blog, I’ll walk through how the Corelight App leverages Splunk’s Common Information Model (CIM) to enhance users' search experience when they are using Corelight data.
The Importance of NDR Detection-in-Depth
Detection Engineering Explained
Best practices for creating custom detection rules with Datadog Cloud SIEM
In Part 1 of this series, we talked about some challenges with building sufficient coverage for detecting security threats. We also discussed how telemetry sources like logs are invaluable for detecting potential threats to your environment because they provide crucial details about who is accessing service resources, why they are accessing them, and whether any changes have been made.
Cyber Threat Modelling
Using Corelight to Identify Ransomware Blast Radius
Over the past few months, ransomware targeting healthcare organizations has been on the rise. While ransomware is nothing new, targeting healthcare organizations, at the extreme, can impact an organization’s ability to engage in anything from routine office visits to life-or-death diagnoses, treatments, and patient care.