Including Digital Risk Protection in Your Threat Detection and Response Strategy
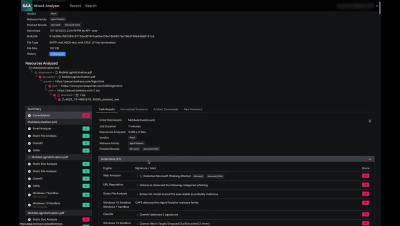
Many organizations focus on addressing the risks within their internal attack surface while overlooking the potential threats created by their external digital footprint on the surface, deep and dark web. This article outlines how companies can significantly mitigate this risk by combining digital risk protection with their detection and response approach.