Beat the Clock: Meet the 5/5/5 Detection and Response Benchmark With Sysdig and Tines
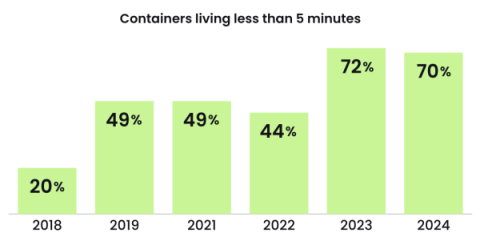
10 minutes to pain. When it comes to cloud security, 10 minutes or less is what bad actors need to execute an attack. Does it mean your business could be at risk if you fail to detect and respond to an attack in less than 10 minutes? Absolutely yes. With more and more sophisticated security attacks actively occurring nowadays, security teams need to hold themselves to a modernized benchmark.