How SOCs can level up their PCAP game with Smart PCAP (Part 2)
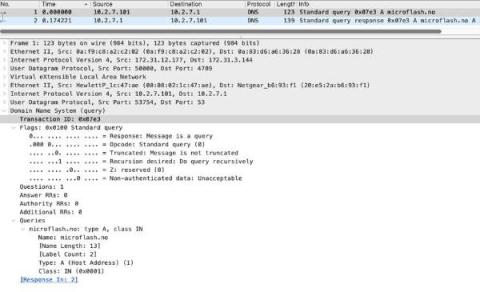
In terms of unencrypted traffic, several highly used protocols lend themselves to logging and can significantly reduce the burden of packet capture without lowering the fidelity of information or the capabilities of analysts.