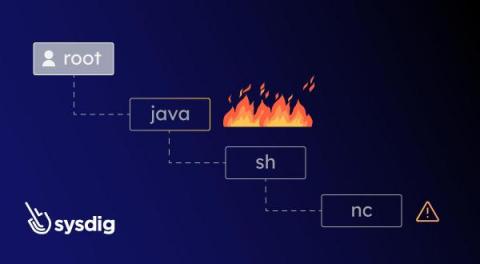
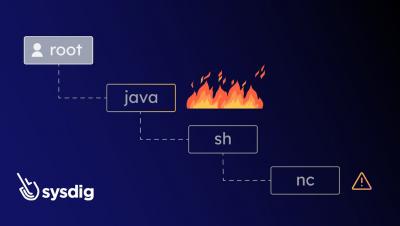
Honeypot Recon: Global Database Threat Landscape
In today's digital era, the importance of securing databases cannot be overstated. As more and more global businesses and organizations rely on DBMS systems to store tons of sensitive information, the risk of targeted attacks and data breaches continues to increase. Therefore, the importance of monitoring and uncovering new actors along with their - often unique - attack techniques and methods is crucial.