Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
Identity Verification APIs Explained: Identity Verification Services in India
Over the last 3 years, Identity Verification in India has seen a marginal boost in the number of verifications conducted digitally. The market growth in the identity verification sector comes as an effect of the disastrous pandemic that caused record-high identity theft, ATOs, and numerous other frauds all initiated through fake identities, resulting in rapid innovation in identity verification API.
The Impact of AI on Cybersecurity: Balancing the Risks and Opportunities
As artificial intelligence (AI) advances, I am seeing a lot of discussion on LinkedIn and in the online media about the advantages it may bring for either the threat actors (“batten down the hatches, we are all doomed”) or the security defence teams (“it’s OK, relax, AI has you covered”).
Does Your Organization Meet the 9 Core Capabilities Essential for Zero Trust in IoT?
Every one of your IoT devices has their own machine identity. But how are these identities the key to achieving Zero Trust IoT project? Today’s PKI (Public Key Infrastructure) vendors have specific solutions for managing non-human identities – machines – like servers, laptops, software applications, API’s and other assets found within a corporate network.
UK's automated self-check-outs using Age Verification API
Self-checkout kiosks are automated devices that enable consumers to scan and pay for their products without the help of a cashier. By this point, we’ve all encountered them. They are frequently seen at supermarkets, department shops, and other retail locations where it is possible to skip tedious manual check-out.
The Ultimate Security Checklist to Launch a Mobile App in Nigeria - iOS & Android
Nigerian authorities have made great strides in data security, and businesses worldwide are taking notice. If you're planning to launch a mobile app in Nigeria, it's crucial that you understand the importance of app security and take steps to ensure that your app meets Nigerian data privacy requirements. We’re aware that data protection can be overwhelming as it requires a holistic approach that incorporates legal, administrative, and technical safeguards.
HIPAA Compliant Mobile App Development: Features, Risks and Checklists
The wide penetration of internet facilities has its imprint on almost all sectors, including the healthcare industry. With most people using smartphones, the demand for online applications is tremendously increasing. As a result, people are shifting towards tele-medication and treatment. However, every successful product has its drawback. Likewise, the popularity of healthcare applications has also captivated more security threats.
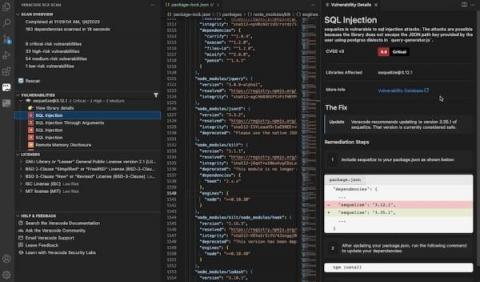
6 Reasons You Need to Run SCA Scans on Projects in VS Code
We love open-source software (OSS). Not only does it save time and effort, but it’s also incredibly rewarding to collaborate with other developers on major projects. Plus, it opens the door for innovation that otherwise wouldn’t be possible at this scale. However, with code comes responsibility, and so it’s imperative to understand the risk OSS libraries carry when we’re integrating them into projects.
Artifactory - Supply Chain Defender
Understanding the basics of Cloud Security: What is Zero Trust & Why does it Matter?
Cybersecurity professionals are tasked with the difficult job of protecting their organization's data from malicious actors. To achieve this goal, zero trust security has become an essential tool for organizations. But what exactly is zero trust? In this post, we’re going to separate signal and noise by disambiguating the term zero trust. We’ll talk about what it is, why it matters, and key takeaways you should have regarding the state of cybersecurity in 2023.