What Does the Future of Password Security Look Like?
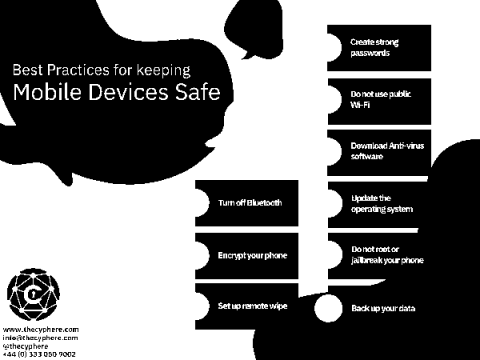
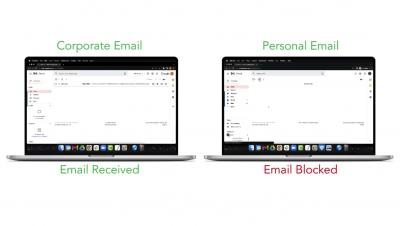
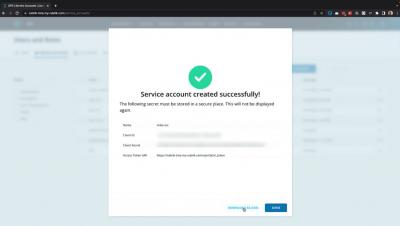
Passwords seem seriously inadequate for security in our lives. It seems they are always getting compromised or hacked through security flaws in apps, and they never seem strong enough. Most of us will be familiar with the headaches of finding the perfect 8-character-long password, only to be told that you’ve used that one before. Even though we know we should use a different password for every secure video conference or site we create accounts for, it’s hard to remember more than one!