Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
Integrate Cloudflare Zero Trust with Datadog Cloud SIEM
Cloudflare's Zero Trust platform helps organizations map and adopt a strong security posture. This ranges from Zero Trust Network Access, a Secure Web Gateway to help filter traffic, to Cloud Access Security Broker and Data Loss Prevention to protect data in transit and in the cloud. Customers use Cloudflare to verify, isolate, and inspect all devices managed by IT. Our composable, in-line solutions offer a simplified approach to security and a comprehensive set of logs.
The Cloud Security Layer Cake: Modern Use Cases for PAM
Warm. Rich. Chocolatey. The way I see it, a proper chocolate layer cake is the best sensory experience a human can have. Let’s go a bit further still: good chocolate cake is the height of human achievement. In the world of enterprise IT, one could say the same of a diverse, purpose-built IT infrastructure. Every enterprise application – whether internal or customer-facing – must run on the right server, virtual machine (VM), container or database for the task at hand.
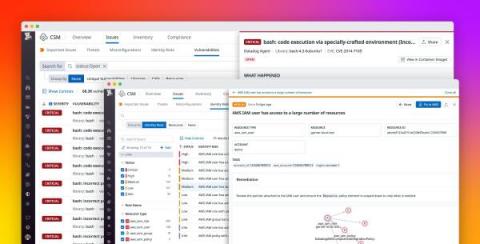
Mitigate identity risks and infrastructure vulnerabilities with Datadog Cloud Security Management
Cloud environments comprise hundreds of thousands of individual components, from infrastructure-level containers and hosts to access-level user and cloud accounts. With this level of complexity, it’s important to establish and maintain end-to-end visibility into your environment for many reasons—not least among them to efficiently identify, prioritize, and mitigate security threats.
Code Mirage: How cyber criminals harness AI-hallucinated code for malicious machinations
The landscape of cybercrime continues to evolve, and cybercriminals are constantly seeking new methods to compromise software projects and systems. In a disconcerting development, cybercriminals are now capitalizing on AI-generated unpublished package names also known as “AI-Hallucinated packages” to publish malicious packages under commonly hallucinated package names.
How Torq Socrates is Designed to Hyperautomate 90% of Tier-1 Analysis With Generative AI
Understanding the California IoT Security Law (SB-327)
2023 Global Cloud Threat Report: Cloud Attacks are Lightning Fast
The second annual threat report from the Sysdig Threat Research Team (Sysdig TRT) is packed with their findings and analysis of some of the hottest and most important cybersecurity topics this year. Threat actors are really embracing the cloud and are using it to their advantage to evade detection and speed up their attacks.
Effective Access and Collaboration on Large Lab Datasets using Egnyte's Smart Cache
The life sciences industry is at the forefront of data-intensive research and innovation. Scientists and researchers rely heavily on the collection, processing, and analysis of vast amounts of data generated by lab instruments. And they are often challenged by errors or confusion in managing data flows that in turn, have a direct impact on the quality of data and corresponding compliance with regulatory requirements.
2 (Realistic) Ways to Leverage AI In Cybersecurity
If you had to choose a security measure that would make the most difference to your cyber program right now, what would it be? Maybe you’d like to get another person on your team? Someone who is a skilled analyst, happy to do routine work and incredibly reliable. Or perhaps you’d prefer an investment that would give your existing team members back more of their time without compromising your ability to find and fix threats? What about human intelligence without human limitations?