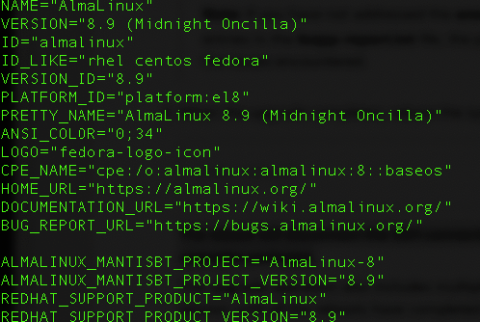
How to Migrate CentOS 7 to AlmaLinux
Jump to Tutorial As of June 30, 2024, CentOS 7 will reach its end of life (EOL). That means it will no longer receive updates, bug fixes, critical security patches, or any new features. It is very important to migrate to a supported operating system to maintain the functionality and security of your systems. AlmaLinux is a reliable alternative to CentoOS. It’s a community-driven enterprise distribution that is binary compatible with Red Hat Enterprise Linux (RHEL).